Introduction
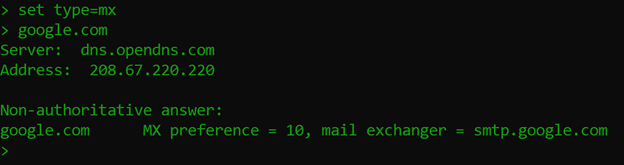
This will be the final installment in this NSLOOKUP Primer series. Last time, I talked about MX & SPF TXT records here, but I didn’t touch on DMARC & DKIM TXT records which are also highly encouraged to help add additional layers of security to your email domain.
Continue reading