Let’s Connect
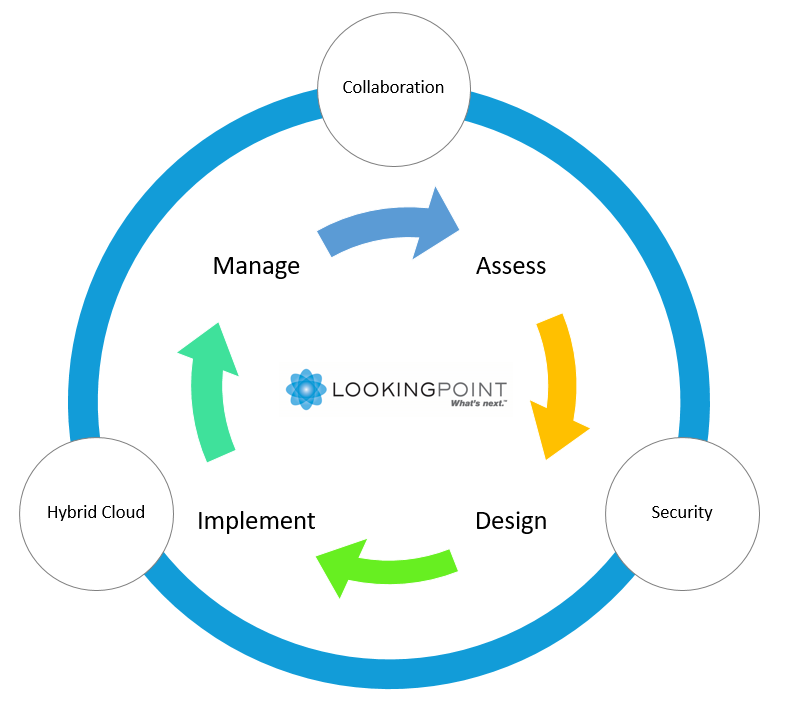
LookingPoint provides a thorough examination of your Network as well as validation of your current configuration and architecture. The review will be focused on network devices and connectivity. LookingPoint will:
The goal of the wireless survey is to validate wireless placement for optimal performance, security, and compliance. The survey will also gather critical wireless information to map out signal, noise and even user performance. High level outcomes include:



Incident based expertise, support and strategic management of your core IT infrastructure - allowing your team to better enable your business.
Customers who want a highly customizable solution, or are restricted due to security and privacy guidelines, an on-premise solution may be the way to go.

Looking Point Inc. 2019