
This is a follow-up Blog to the outstanding high level introduction to SASE presented by Lookingpoint President, Sean Barr, if you haven’t seen it, check it out here! For anyone interested in getting into the weeds a bit further, feel free to stick around!
When I first saw the technical acronym ‘SASE’, I couldn’t help but think of a plucky neighbor from a ‘90s sitcom, acting lively, bold, and full of spirit. I quickly learned it stands for ‘Secure Access Service Edge’, and is a technical term coined by Gartner in 2019. Incidentally, Gartner also defined the SIEM (Security Incident and Event Management) acronym and standards which has become widely adopted by vendors across the globe, so you know they know their stuff! As mentioned earlier SASE stands for ‘Secure Access Service Edge’, but what exactly is a ‘Service Edge’ anyway? Service edge refers to global point of presence (PoP), IaaS, or colocation facilities where local traffic from branches and endpoints is secured and forwarded to the appropriate destination without first traveling to data center focal points.
Gartner describes SASE as combining network security functions such as Secure Web Gateway (SWG), Cloud Access Security Broker (CASB), Firewall as a Service (FWaaS), and Zero Trust Network Access (ZTNA) with WAN capabilities (SDWAN) to support the dynamic secure access needs of organizations. In other words, it’s an architecture that combines networking and security together to provide secure network access to the users, regardless of their location and device type, and regardless of what they’re accessing.
The COVID outbreak forced the shaping of flexible access requirements seemingly overnight. Users and applications have become decentralized, much faster than anyone predicted. Effectively flipping the traditional model upside down. Who remembers the 80/20 rule? Well, forget it, try 20/80 now! The big question is, how do we secure our users, devices, data, and applications now that they are scattered into the wind? The image below captures this migration to cloud well, even branch and HQ locations aren’t immune to the shift of traffic to the cloud.
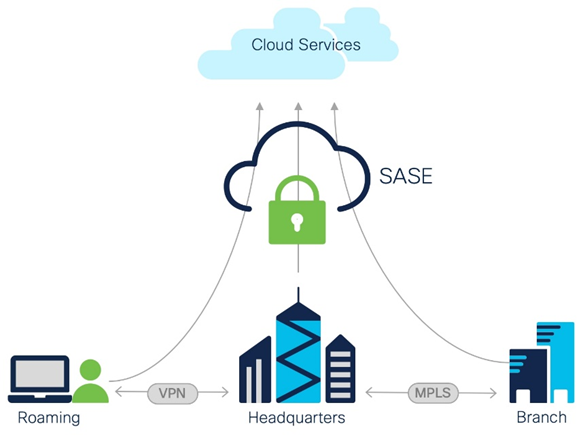
Every vendor under the sun is dealing with this shifting landscape, and while SASE was once considered a niche area of focus, it has now become a dominant focus for many vendors and organizations. To Gartner’s credit, they’ve defined the structure which has helped standardize offerings. Even so, you may find different vendor approaches to satisfy the broad definition. Some may implement SASE as a single native solution while others offer it as a combination of technologies. Since I’m a huge Ciscohead, this blog will focus on their solutions. (Cisco, if you’re reading, send me swag! :D)
Cisco has a solution that addresses each category defined by Gartner (and some others to enhance/compliment even further, depending on how deep you want to go down the rabbit hole of security). Their holistic approach breaks SASE into the three C’s, Connect/Control/Converge. These cover the broad definition defined by Gartner, but also get much more granular.
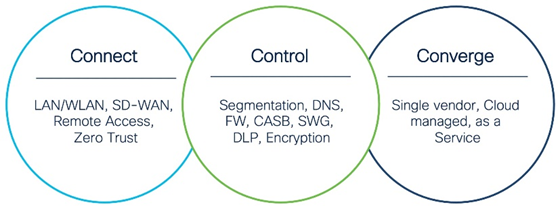
- Connect – Focusing on the networking aspect, getting packets from point A to point B, securely, and with intelligence. As they put it, “seamless connection to applications in any environment from any location”. This includes SDWAN and Remote Access services, ideal for Home/Branch/Roaming Users.
- Control – Simplifies security, streamlines policy enforcement, and increase threat protection via a single, cloud-native service. This is provided through their Cisco Umbrella services as well as some other more specific offerings.
- Converge – Unites security and networking through a flexible, integrated approach that can scale. It’s the value Cisco brings that ties all the components together.
Let’s look at the products offered under each Cisco SASE architecture Component
CONNECT
Software-defined wide area networks (SD-WAN)

If you haven’t heard of Cisco’s SD-WAN, you must be living under a rock! In short, Cisco SD-WAN is a cloud-delivered overlay WAN architecture connecting branches to data centers and multicloud environments through a single fabric and single pane of glass. In simple terms, it’s a router that builds multiple dynamic overlay tunnels between locations using your internet/MPLS/Whatever (underlay) connections and controls traffic based on link speeds/health and performance policies, it’s neat.
- Advanced application optimization that delivers a predictable application experience. Easily create policies for traffic priorization. Enhance the experience with the following add-on components.
- Cisco ThousandEyes extends application visibility into the internet and cloud for actionable insights. Users complaining about App performance over the WAN? Well, this is the tool to use to find issues that are normally outside the network teams’ realm of visibility.
- Cisco vAnalytics offers visualized performance insights into the underlying SD-WAN network.
- Multilayered security that provides the flexibility to deploy specific security in the right place, either on-premises or in the cloud.
Zero Trust with Cisco Duo

Chances are you’ve probably seen or used Duo, it’s a ubiquitous MFA service which lets you verify the identity of all users — before granting access to corporate applications. You can also ensure devices meet security standards, develop, and manage access policies, and streamline remote access and single-sign-on (SSO) for enterprise applications. Here are some highlights
- The go-to MFA product for remote access VPN and enterprise applications.
- Can leverage your Identity Providers or act as an Identity Provider
- New Duo access policies that enforce application access based on device health. (Posture checks!). Also provides additional endpoint information provided in the Duo Admin Panel.
CONTROL
The elephant in the room is the powerhouse that is known as Cisco Umbrella, it’s a huge component of the Cisco SASE offering. It checks off several SASE core components. This SASE blog is focusing on what Cisco deems their official SASE suite offering, but it’s worth noting Cisco does has other products that fulfil some aspects of what is considered a SASE use case. This list does not cover those overlapping products, such as Cisco Cloudlock (CASB), Cisco Secure Workload (Formally Tetration), or Cisco Secure Network Analytics (Formally Stealthwatch), so keep an eye out for future blogs which cover those products in more detail. Today we’ll be focusing on the traditional products Cisco defines as part of its SASE package.
As depicted by the image below, with a wave of the hand, Cisco addresses several core SASE components with Cisco Umbrella.
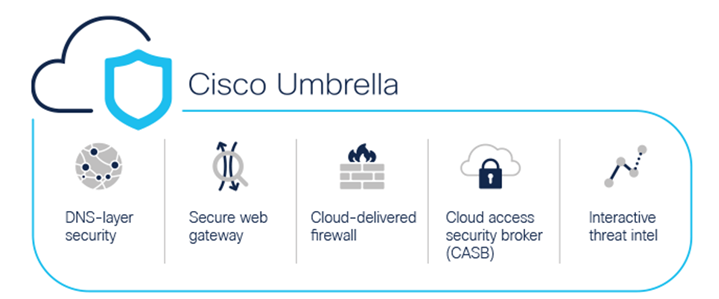
Domain name system (DNS) layer security
A foundational element of the Cisco SASE architecture! Prior to Cisco’s acquisition, it was called OpenDNS, and to date it has probably saved millions of dollars by mitigating malicious activity. In its most basic form, which is still offered for free by Cisco, is it’s a DNS proxy feature. Simply put, you direct DNS requests to their public servers and they’ll filter out the bad actors. As Cisco puts it, “Cisco Umbrella helps businesses of all sizes secure direct Internet access (DIA), secure cloud applications, and extend protection to roaming users and branch offices. Cisco Umbrella blocks requests to malicious and unwanted destinations before a connection is even established.”. It’s also integrated into their other products to provide defense in depth. For example, it can be leveraged by Meraki. You can even add Umbrella module to Anyconnect and push to users through Firewall Connection Profiles, providing protection to even the most technically challenged end-user. 😊
Some Highlights of the DNS-layer protection offered by Cisco Umbrella:
- By enforcing security at the DNS and IP layers, Umbrella blocks requests to malware, ransomware, phishing, and botnets before a connection is established.
- It can be deployed by either directing DNS directly to Cisco Umbrella DNS servers or leveraging internal virtual appliances. The VAs provide internal IP visibility, allowing you to track down malicious or inappropriate traffic within your network to a specific IP address. They intelligently forward public DNS queries to Cisco Umbrella's global network, and local DNS queries to your existing local DNS servers and forwarders.
- Every public DNS query sent to Umbrella is encrypted, authenticated, and includes the client's internal IP address when using VAs.
- Leverages threat intelligence from Cisco Talos. This means Umbrella uncovers and blocks a broad spectrum of malicious domains, IPs, URLs, and files used in attacks to deliver the best protection for all users, on-prem or remote.
- You can enforce the appropriate level of control and security for different networks, locations, or user groups from a single management console.
Secure web gateway (SWG) & Cloud-delivered firewall
Cisco Umbrella includes a secure web gateway (SWG) that uses a cloud-based proxy to log and inspect all your web traffic for greater transparency, control, and protection. Cisco Umbrella Secure Internet Gateway (SIG) packages include even more advanced security coverage across all traffic (DNS, IP, web, and more). SIG includes a Secure Web Gateway (“SWG”) to analyze all traffic on web ports (IP or domain destinations), and a Cloud Delivered Firewall (“CDFW”) that layers on a cloud-based firewall in addition to SWG.
- Real-time inspection of inbound files for malware and other threats
- Advanced file sandboxing
- Full or selective SSL decryption to further protect against hidden attacks
- Blocking of specific user activities
- Content filtering by category
- Layer 7 application visibility and control (CDFW)
- Visibility and control for Internet traffic across all ports and protocols (CDFW)
- Customizable IP, port, and protocol policies in the Umbrella dashboard (CDFW)
Cloud access security broker (CASB) functionality
A Cloud Access Security Broker (CASB) acts as an intermediary between cloud providers, cloud-based applications, and cloud consumers to enforce an organization’s security policies.
One of the main objectives of a CASB is to keep an organization’s data safe and secure. Umbrella App Discovery offers the following CASB functions:
- Extended visibility into cloud apps in use and traffic volume
- App details and risk information
- Capability to block/allow specific apps
More Good Stuff!
As mentioned before, Cisco can get more granular with the broad SASE term. Things like segmentation and enhanced CASB services may be required over what Cisco Umbrella can provide, in which case you’d want to investigate the products listed below. Keep an eye out for my next blog, which will focus on Cisco Secure Analytics (Formally known as Stealthwatch).
- Cisco Cloudlock – is a cloud-native cloud access security broker (CASB) that helps you move to the cloud safely. It protects your cloud users, data, and apps. Cloudlock's simple, open, and automated approach uses APIs to manage the risks in your cloud app ecosystem.
- User and Entity Behavior Analytics
- Data Loss Prevention (DLP)
- App Security
- Cisco Secure Analytics – Secure Network Analytics provides comprehensive network visibility. It’s multi-faceted and can be licensed for on-prem and/or cloud-based environments. I’ll keep this highlight short as I’ll be dedicating an entire blog to it in the future. Here’s a rather concise summary from Cisco, “The solution detects advanced threats and early indicators of compromise by identifying all the entities in the network, modeling network behavior and alerting on behavioral anomalies that are security relevant and should be investigated. This includes a virtual appliance(s) that is installed locally in the network to collect IP metadata, such as Netflow, generated by your switches, routers, and firewalls, additionally it can generate flow records by attaching to network ports. The virtual appliance transmits the locally collected data to the service where an advanced model is kept for every entity.” Coupled with Cisco Tetration, you can put together a very concise micro segmentation architecture.
- Cisco Trustsec – TrustSec is an umbrella term for security improvements to Cisco network devices based on the capability to strongly identify users, hosts, and network devices within a network, through the use of Security Group Tags (SGTs). The SGT denotes the endpoint’s access rights, and all traffic from the endpoint will carry the SGT information. The SGT is used by switches, routers, and firewalls to make forwarding decisions. This ensures the network access policies are defined by the identity of the user or device, and not simply by where they’re connecting (traditional handled with VLANs and NAC). I’ll publish more on this awesome approach to network segmentation in the future.
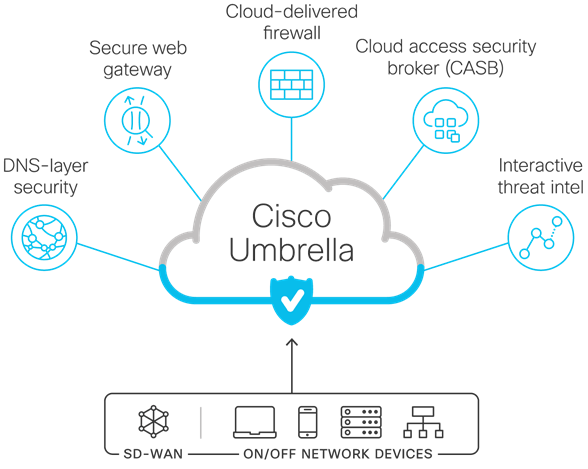
CONVERGE
The solutions presented are delivered ‘As a Service’ and provide the means to protect your users, devices, and applications, all from a powerful UI hosted by Cisco, with minimal client/server requirements.
In Conclusion,
What’s the gold standard for securing data, applications, and workers everywhere? Cisco’s Secure Access Service Edge (SASE) solutions, and family of other Cisco products in the security and analytics space! (gimme, gimme, gimme that swag, Cisco!! 😉) I hope you enjoyed reading this as much as I enjoyed writing it, and I hope it helps you decide you with your SASE decision making!
As always, if you have any questions on getting a SASE solution set up for you and your business and would like to schedule a free consultation with us, please reach out to us at sales@lookingpoint.com and we’ll be happy to help!
If you want to hear even more about SASE, we talked to Cisco Technical Solutions Architect, Mark Kasper, who took us through what SASE (Secure Access Service Edge) is and why businesses should consider introducing this into their IT environment. Listen here!
Michael Lorincz, Network Engineer




