What if you could see into the future and knew when an attack on your network was coming and were able to stop it, or at least mitigate its impact?
Good news, you can!
Every year Cisco releases their Annual Cybersecurity Report and this year's report examines topics, data and analytics aligned with three general themes:
- The sophistication and impact of malware
- How encryption is being used by attackers to evade detection and weaponize cloud services
- Gaps in network security stemming from unpatched or unmonitored IoT devices
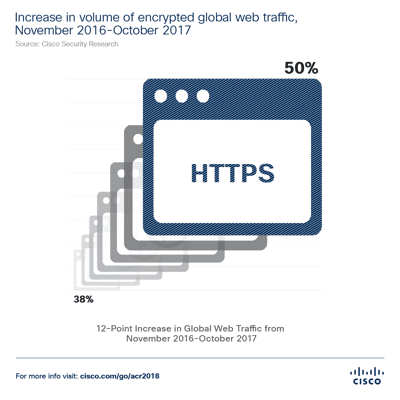
In 2017 malware - specifically ransomware - was the threat that monopolized security discussions and sat at the top of every IT security professionals watch list. Ransomware dominated the headlines from WannaCry and Nyetya in 2017 to the SamSam malware infection that periled the city of Atlanta in April this year. Another threat causing challenges for security professionals is the expanding volume of encrypted we traffic. Encrypted global web traffic increased by 12 points from October 2016 - November 2017 according to Cisco threat research. Phishing attacks are also threats still on security radar. While phishing attacks seem to be an "old" threat, IT teams and users should still be vigilant in monitoring for them.
 As more of our data and applications are shifting to the cloud, it is important for IT teams to evolve and adapt their securities from the traditional network perimeter approach to tactics suited for cloud defense. It's important to protect your network across the entire attack continuum and deliver consistent and integrated security across your multi-cloud environments. Cloud-based security best practices include:
As more of our data and applications are shifting to the cloud, it is important for IT teams to evolve and adapt their securities from the traditional network perimeter approach to tactics suited for cloud defense. It's important to protect your network across the entire attack continuum and deliver consistent and integrated security across your multi-cloud environments. Cloud-based security best practices include:
- Extend data center performance, control access to your data center, and limit how data is handled. Enforce governance and compliance with automated security policies. Monitor compliance with centralized management.
- Provide a consistent user experience across devices, both on and off premises. Defend against threats, no matter where users are. Extend protection to users when they are off your network or VPN.
- Deploy security solutions easily across all environments. Integrate security across all cloud deployments. Gain consistent protection, removing vulnerable coverage gaps.
- Connect new users and devices quickly with the right access. Maintain protection of remote users and devices automatically. See into user behavior and device status.
Lumeta refers to a policy or segmentation violation or unauthorized or misconfigured connection that allows traffic to be forwarded to a location on the Internet as a "leak path". Devices, including routers and switches, that are misconfigured are vulnerable to attack and leave your entire infrastructure susceptible. Monitoring for leak paths is critical to prevent exploitation of your infrastructure. There are tolls for automation that can provide security analytics and insights to potential leak paths

According to Cisco’s 2018 Security Capabilities Benchmark Study more than 53% of all cyber attacks resulted in financial damages of $500,000 or more. The areas organizations are finding most challenging to defend area mobile devices, user behavior and public cloud data.
 Implementing strategic improvements to your security architecture in addition to adhering to security best practices is the best way to reduce your threat risks, slow attack spread in your environment and give you more visibility into potential threats. When evaluating your existing security infrastructure and possible improvements Cisco suggests considering all of the following:
Implementing strategic improvements to your security architecture in addition to adhering to security best practices is the best way to reduce your threat risks, slow attack spread in your environment and give you more visibility into potential threats. When evaluating your existing security infrastructure and possible improvements Cisco suggests considering all of the following:
- Implementing first-line-of-defense tools that can scale, like cloud security platforms.
- Confirming that they adhere to corporate policies and practices for application, system, and appliance patching.

- Employing network segmentation to help reduce outbreak exposures.
- Adopting next-generation endpoint process monitoring tools.
- Accessing timely, accurate threat intelligence data and processes that allow for that data to be incorporated into security monitoring and eventing.
- Performing deeper and more advanced analytics.
- Reviewing and practicing security response procedures.
- Backing up data often and testing restoration procedures—processes that are critical in a world of fast-moving, network-based ransomware worms and destructive cyber weapons.
- Reviewing third-party efficacy testing of security technologies to help reduce the risk of supply chain attacks. • Conducting security scanning of microservice, cloud service, and application administration systems.
- Reviewing security systems and exploring the use of SSL analytics—and, if possible, SSL decryption.
Cisco also suggests considering the adoption of advanced security technologies, such as machine learning and artificial intelligence to stay ahead of the evolving threats.





