Recently we had a business owner come to us asking for help recovering their files from a ransomware attack.
Just a quick refresher - ransomware is a type of malicious software designed to hold a user’s files (such as healthcare records, financial contracts, software codes, and other documents) for ransom by encrypting them and demanding the user pay a fee to decrypt them. In 2017 ransomware was the threat that monopolized security discussions and sat at the top of every IT security professionals watch list. Last year headlines were dominated by ransomware attacks from WannaCry and Nyetya. This year attacks are decreasing in volume but increasing in sophistication (Barkly), but are still finding their way into the headlines with the SamSam malware infection that periled the city of Atlanta in April 2018.
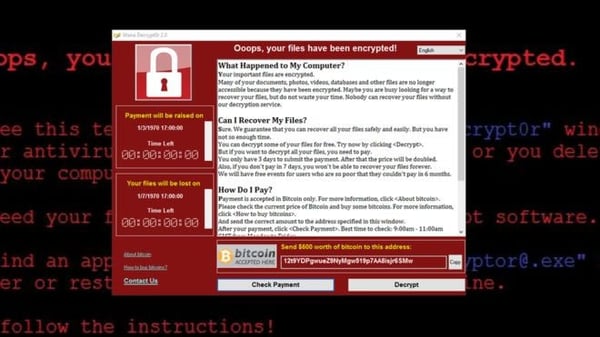
This particular organization had a critical server for their business accessible on the Internet over Microsoft Remote Desktop Services to allow users to access this machine remotely for a real business need. We believe remote desktop services was the attack vector. When the system was compromised, all files except critical windows files needed to actually boot were encrypted and there was just a note to email the scammer to decrypt the files. There were no backups of this machine, which left no real way to restore the files without the decryption key. With no backups to use for restoration our team did research and try all known ways to decrypt the files without success. Unfortunately, there are a lot of variants of this particular ransomware out there and a solution for one didn't necessarily work for the rest. With no way to decrypt the files and no backups available the business was forced to pay the ransom for the decryption key.
The challenges with paying a ransom - outside of morale opposition - include payment options (most scammers prefer bitcoin which is difficult to buy quickly if you don't already own it), the risk that the scammers do not send a decryption key once payment is received as well as the risk that the decryption key does not decrypt all files. In this scenario bitcoin was already available for payment, the hackers sent the decryption key (even though the was no recourse if they didn’t), and the key decrypted all files with a few exceptions…enough that the primary application would not launch and required a reinstall, but the database was intact. All things considered this is a best case scenario for a ransomware recovery, but this attack could have been prevented by simply implementing 2 factor authentication to stop unauthorized users from accessing it, or by putting this server completely behind the firewall and using a VPN solution to access internal resources.
Two-factor authentication, firewalls and VPN are only a few solutions we recommend to protect your network from ransomware attacks. A few best practices to reduce your risk of falling victim to a ransomware attack are:
- Backup your data: if your network is breached data backups will minimize data lost and won't leave you vulnerable to being held ransom
- Routine system updates: regular software updates and system patches reduce your vulnerability to be exploited
- Secure your network: A layered security approach combines multiple mitigating security controls (from the endpoint to the DNS layer) to protect resources and data.
- Segment network access: dynamically controlling network access helps reduce exposure across the network if it is compromised.
Security tools and data backup measures we recommend to help protect your network from a ransomware attack are:
- Two-Factor Authentication: Two-factor authentication is all about checking credentials - Are you who you say you are? Traditionally, a user name and password are used to log into a secure system. Two-factor authentication provides an additional layer of security, in the form of something you physically have, to be able to log into the system. This can be a physical token in the form of a smart card or embedded into a key fob or a smartphone.

- Virtual Private Network: A Virtual Private Network (VPN) extends your private network across a public network and allows employees to securely send and receive data on that public network as if they were on the private network. VPN solutions provide IT teams with the visibility and control identify who and which devices are accessing the extended enterprise and to deliver a secure mobile experience for users.
- Umbrella Roaming DNS Protection: Cloud-delivered security at the DNS and IP layers allows security teams to protect any device, anywhere - without needing to install hardware appliances or maintain software. Use the Internet's infrastructure to block malicious destinations before a connection is ever established, and provides visibility into Internet activity across all devices, over all ports, even when users are off your corporate network
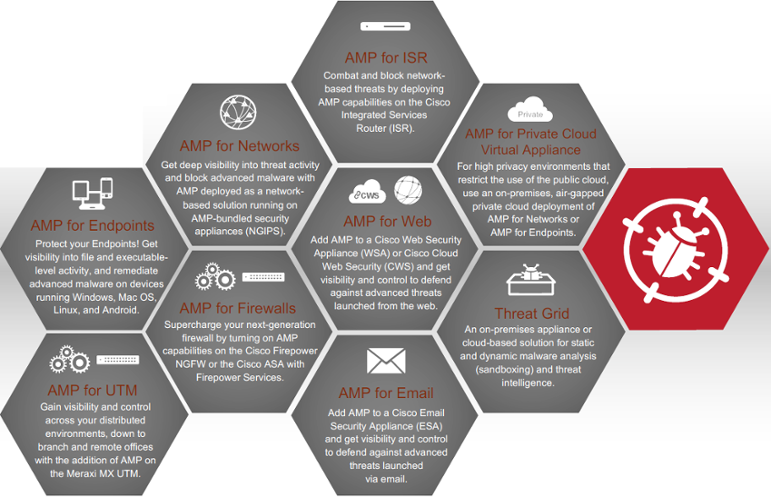
- Advanced Malware Protection (AMP) : Protect your environment before, during and after an attack. AMP not only prevents breaches, it also provides the visibility, context, and control to rapidly detect, contain, and remediate threats if they evade front-line defenses and get inside, all cost-effectively and without affecting operational efficiency.
- Identity and Authentication: Cisco Identity Services Engine (ISE) is a single policy control point for your entire enterprise (Wired, Wireless, VPN). ISE brings together the industries most rigorous identification and access control technologies in one simple automated solution. ISE looks at user, time, location, type of device, and even its health for compliance, and then applies relevant policies to control what resources can be accessed.
- Data Backup and Recovery: Backup data for recovery on physical and virtual environments. Having data backups will allow you to restore to the last backup and minimize data lost (depending on your backup RPO (Recovery Point Objective) the loss may be hours of data or days), but you data will not be lost or vulnerable to being held ransom.
Increased awareness, improved security measures and reliable data backups have all contributed to ransomware's decline, but we still do see organizations that don't have the appropriate backups and security measures in place to protect themselves from an attack. If an organization without data backup is breached the only thing there is to do to get the data back is to pay the ransom to the attackers. This is why it is critical to backup your data, even if you have the security tools in place to help protect you against a ransomware attack - no one is completely invulnerable. We encourage anyone reading this blog to go and do a quick check of your security systems in place and to make sure your data is backed up.
Written By: Eden Reid, LookingPoint Marketing Manager



