Hello all! Today we will be talking about Mobility Anchoring with Cisco Wireless LAN Controller (WLC). While this concept has been around for a while, and is commonly used for guest networks, I have used it for several other reasons. But first let’s go over the premise of mobility anchoring.
Cisco defines mobility anchoring as: Mobility Anchor, also referred to as Guest tunneling or Auto Anchor Mobility, is a feature where all the client traffic that belongs to a WLAN (Specially Guest WLAN) is tunneled to a predefined WLC or set of controllers that are configured as Anchor for that specific WLAN. This feature helps to restrict clients to a specific subnet and have more control over the user traffic.
To break that down further, it is tunneling WLAN traffic from a local controller to a different controller within the same mobility group, for a different entry point into the network. As the Cisco definition states, it is great for guest traffic. It allows you to have a different WLC setup within the DMZ to allow for guest traffic directly out of the internal network.
First requirement is that both the local WLC and anchor WLC need to be in the mobility group. This requires reachability between the two WLCs. Therefore, if being used to anchor guest traffic on the other side of a firewall, you will need to open up traffic on the firewall for two way communication.
There are plenty of guides out there for setting up guest anchor controllers, and I do not want to beat that horse, so I am going to shift that thinking slightly with an example of a proposed design. As I have mentioned I have used mobility anchoring for different solutions in the past and let’s explore that more.
Let’s imagine you work for a company with a data center, a corporate office, and many smaller remote sites, like I did for years. We had metro-Ethernet connections with all traffic being sent back to main data center. Now with the growing demand for wireless networks with all types of devices, securing those networks becomes increasingly difficult. I happened to work within the healthcare industry, and needed to segment off some devices to provide additional security. Now think about the administrative costs alone for deploying multiple firewalls at locations for WLANs that are only intended to serve a few clients each.
The solution I came up with was to use… Mobility Anchoring! How does a technology that is intended for guest traffic to be placed in the DMZ help this case you ask? Simple, when we use mobility anchoring as way to change the entry point into the network, you can then use that to control where the security for that network lives as well. In my case it was at our data center where we had nice beefy NGFW (Firepower Threat Defense) firewalls, and a core network infrastructure to allow for bandwidth. With the ability to tunnel traffic back to a central location and secure the VLAN that those clients will ultimately use as a network entry point, we were able to save time and money by not needing to deploy different firewalls to each location and setup new networks for all.
Now let’s walk through this design to better understand this. With my scenario, we have a main data center with multiple branch locations as in image below.
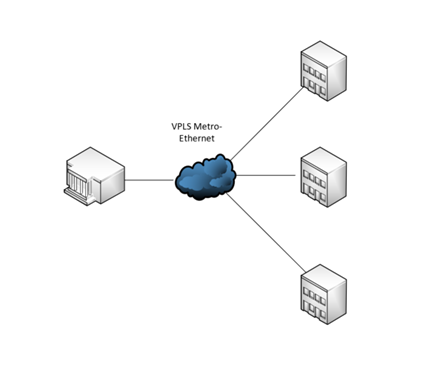
Each location has an existing WLC and we want to add additional WLANs, but need them secured with a firewall. Wouldn’t it be easier to have all that new WLAN traffic run through a single firewall, and all of it to be secured at all locations? My proposed design was:
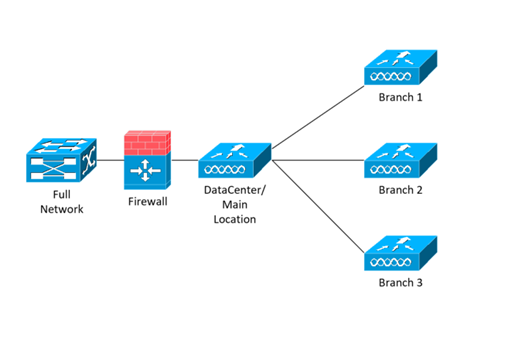
With using Mobility Anchoring, to route those WLANs back to the central location, we are now able to secure that VLAN where the anchor WLC enters the network. The mobility tunnel will send all traffic on the remote WLAN tunneled back to the anchor point, and from there it can be allowed or denied access to different networks of your choosing through traditional firewall rules. This approach now allows for a standardized deployment of WLANs across multiple sites without the need of additional firewalls to provide the same security requirements to remote locations.
This fit our needs exactly, and ended up becoming our standard deployment for additional WLANs for all remote locations. Some key factors to think about when setting this up are, bandwidth across your WAN, and the number of clients you will be connecting. If you are tunneling all traffic back to a central location, you might want to think about setting limits on the local and anchor controller for bandwidth. Additionally, you will want to think about the number of clients you are connecting to that anchor controller, and size it correctly with both clients and uplink bandwidth.
As always if you have any questions on the Wireless Mobility Anchoring and would like to schedule a free consultation with us, please reach out to us at sales@lookingpoint.com and we’ll be happy to help!
Armando Muscaritolo, Network Engineer




