In my last nslookup blog, I talked about some basic DNS troubleshooting. If you missed it, here’s the link. This time, I wanted to dive in to how I use nslookup for email info gathering and troubleshooting.
MX Records
Let’s start with MX Records, when you send an email, your email server takes each recipient’s domain & does a DNS lookup to determine where to send your email. Here’s how we can check for ourselves.
Open NSlookup, type “set type=mx” then type in a domain to see what mail server(s) is/are registered for that domain.
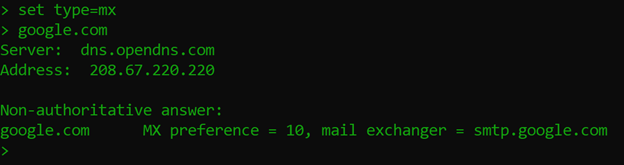
TXT Records
Next, let’s take a look at txt records. Once you set type=txt and put in a domain, you may get a number of responses. Let’s focus on a couple that can help us when we’re troubleshooting or securing email.
SPF (Sender Policy Framework) Records
SPF records are a form of spam control. It’s a DNS record that tells the world which servers you authorize to send mail on your behalf. This is a DNS lookup that a receiving mail server would look up to verify that the server they just got an email from is allowed to send for that domain (and not spoofed). If you want the definitive source for SPF records, check out the RFC. For now, let’s take a look at Google’s SPF record.
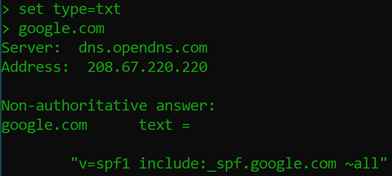
So to break this down:
v=spf1 is telling us this is the first “version” of the spf entry. Since most TXT records in DNS have a 255 character limit, sometimes multiple entries are needed, so you may occasionally see v=spf2 or even v=spf3 as well.
Include: is a mechanism to identify which servers to include in our list of allowed senders. It’s common to see multiple Include statements. Other available mechanisms are ip4 (IPv4 address or range), ip6 (IPv6 address or range), DNS references such as “a” (include all of the domain’s a records as allowed senders), “mx” (allow all mx records as allowed senders). There are some other mechanisms as well that will allow you to get really fancy with your SPF (check out the RFC if you want to know more).
_spf.google.com is a DNS name of server(s) to include. In Google’s case, that is referencing another SPF record (which is another way to get around the 255 character limit), so let’s do another nslookup
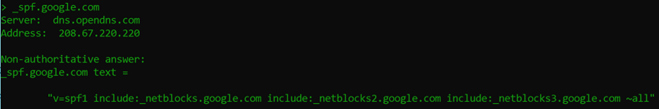
In this case, this is a set of SPF records under another SPF record. Let’s take a look at the next clue in our little mystery.
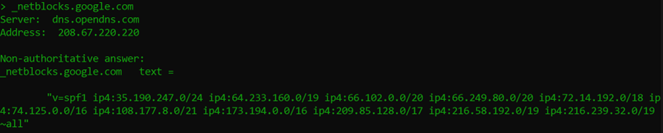
Now we’ve gotten to the IP ranges that are allowed to send email from google. The other netblocks have even more records, but you can see how that 255 character limit might require some planning.
all is typically what ends an SPF record. It is the final check that tells a server checking this record how to handle emails all other checks that haven’t matched what’s specified in the SPF record. Anything else in the SPF record afterwards will be ignored.
~ is a qualifier (in this case used on all) and tells the server checking your SPF record that any check matching should be considered a “soft fail” meaning SPF is telling the checking server that the host is probably not authorized. Other qualifiers are “+” (pass), “-“ (fail, or DEFINITELY not authorized), and “?” (neutral). All records without a qualifier are treated as a + (pass).
It just so happens that LookingPoint offers multiple IT services if you’re interested. Want more information, give us a call! Please reach out to us at sales@lookingpoint.com and we’ll be happy to help!
Ryan Alibrando, Managed Services Team Lead




