Say hello to Cisco’s RADkit
How would you like a tool that can save you time with TAC cases and gives you an avenue of automation and time savings for your entire Cisco environment? If that sounds good, you should give RADKit a look.
What is RADKit?
RADKit is Cisco’s “Remote Automation Development Kit” that provides both you (and TAC) many automation opportunities for management and troubleshooting of your environment. It consists of a service and a python-based client that each connect securely to a cloud service maintained by Cisco. It will run on a Windows, Mac, or Linux machine inside your environment, and you (or TAC) can run a client from anywhere to take advantage of it. The best part is, you have complete granular control over access and your data which is only stored locally. The cloud seems to be used as a method of authentication.
Installation
The Installation Process is covered in depth with a video available at https://radkit.cisco.com and takes less than 10 minutes.
Adding Devices
Once installed, you can access the RADkit service locally (it opens a browser to https://localhost:8081), or remotely via IP address or FQDN on port 8081 by default. When you login, you’ll see your service serial number - copy that somewhere as you’ll need it later for the client. Once on the service browser portal, you can add the devices that you want to have available via the tool and choose the management protocol(s)
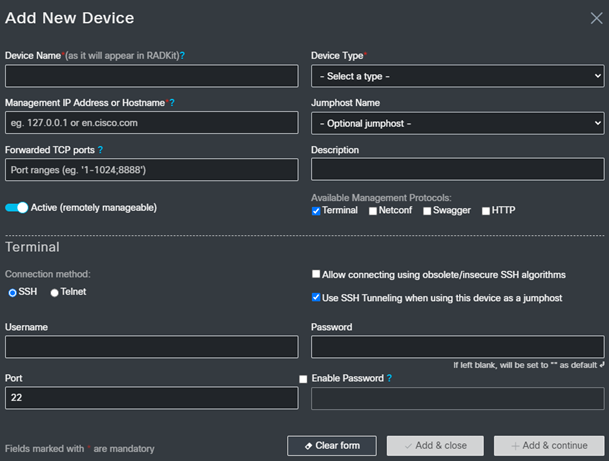
As you can see from the optional device types, there are many cisco technologies available.
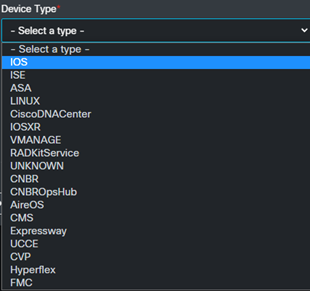
This is also where you can create new users and give them access for a set amount of time so you don’t have to remember to come back and disable accounts.
Logging in via the client
Once your server is installed and you’ve added a device or two, it’s time to try out the client. Starting the client takes you to a python prompt, and you’re provided with several examples to help you get connected.
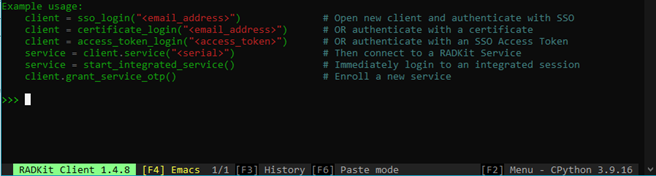
I just followed the examples and ran the following:
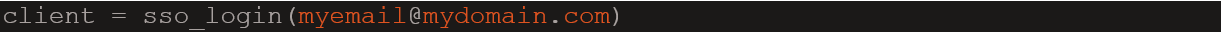
That popped up a new browser tab to authenticate with Cisco’s SSO that looked like this:
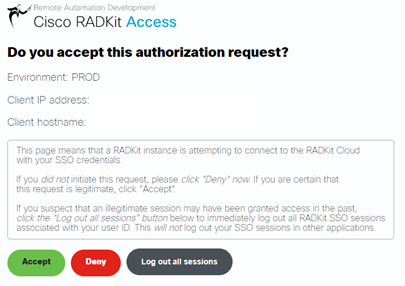
After authenticating, I was prompted to accept the authorization
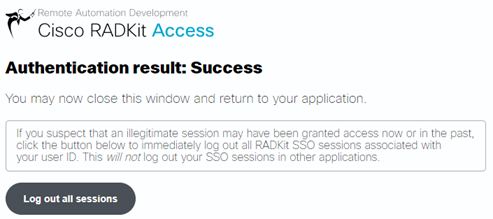
After clicking Accept, I received this message:
The next step after that was to connect to the service using the following command (this is where you use the serial number you got earlier) and then we can reference it as “service” from this point on to use the built in functions.

and if all goes as planned, you should be ready to interact with your devices through this interface.
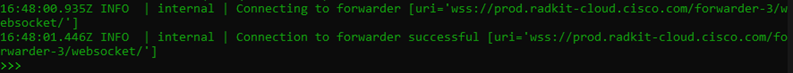
Using the Client
As I’m still learning and exploring myself, I’m only going to share a few examples, but expect that I’ll have more in the future to show you.
First, you can run the following command to show you the devices you’ve added and which management you’ve set up.
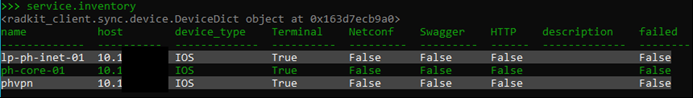
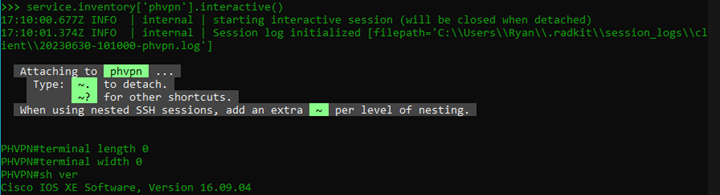
You can also choose one of your devices to interact with which in this case is essentially a built in SSH client, only the credentials are all securely stored from when I added devices.
What’s really cool is that you can grab information from multiple devices at the same time, store it in a python variable, then parse it, which gives you some pretty fantastic opportunities to save a LOT of time by creating a script that you can run against all your devices not just once, but whenever you want. You can start to see the power of the tool in TAC’s hands and how they may be able to have a store of these scripts to quickly get to the bottom of a problem.
In this example, I execute the “show version” command on each device in my inventory, that information is stored in a dictionary with the device and show version output.
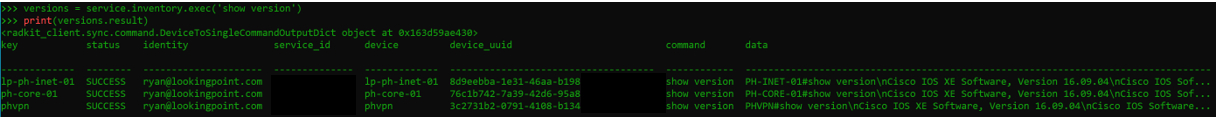
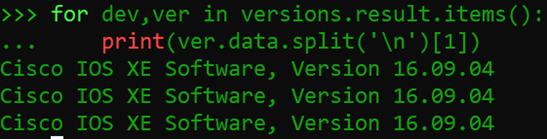
In this example, I execute the same command, then use python to give me just the data I want. So for each device (dev) and version info (ver) in the results, I split the data (ver.data) on each new line character (‘\n’) and pull just the 2nd line of the data ([1]) (data starts at line 0, so I’m calling line 1) to show the version.
If you have some familiarity with working with Python, you can begin to see how powerful a tool this might be to utilize libraries built by Cisco to interact with their devices.
Check out cisco’s RADKit Videos Here:
https://radkit.cisco.com/videos.html
CONCLUSION
I’m looking forward to learning more and trying out new things with this tool. One thing I’ve read that I’m excited to try out is to open a TAC ticket and tell them that I have this in my environment and see if the engineers are able to solve the problem more quickly AND not have to take over my computer. This is one of the main points they mentioned in the videos and I’m hopeful it could be a big time saver (fingers crossed). I hope you’ll give RADKit a try especially with the low time and cost investment necessary and I’ll try to put out another blog with some more tricks and things you can do with this tool down the road.
It just so happens that LookingPoint offers multiple IT services if you’re interested. Want more information, give us a call! Please reach out to us at sales@lookingpoint.com and we’ll be happy to help!
Ryan Alibrando, Managed Services Team Lead




