Within Cisco Umbrella Secure Internet Gateway (SIG) many features are at our disposal, such as Secure Web Gateway, DNS-Layer security, Cloud-delivered firewall, and many more. Information about Cisco Umbrella SIG can be found here.
https://umbrella.cisco.com/products/sig-product
In a previous blog I’ve talked about Cisco Umbrella DNS-layer and how to secure your organization at the DNS level. In today’s blog I wanted to highlight Cisco Umbrella Cloud-delivered Firewall (CDFW). It is a Cisco Umbrella SIG feature and requires some prerequisites before deploying successfully.
Once all these requirements are meet, we will need to create an IPsec tunnel between our device and the Umbrella headend. In the lab that I used a CSR device was provided to me. Umbrella online guides provide addition information on how to deploy to ASA, FTD, AWS, and go into further detail on IPsec tunnel and routing configuration.
https://docs.umbrella.com/umbrella-user-guide/docs/tunnels
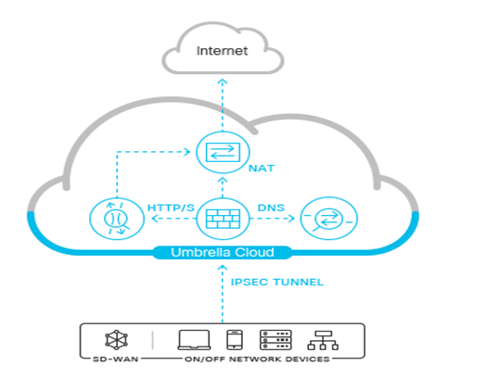
In our Umbrella dashboard we will want to navigate to the location Network Tunnels. Here we will setup our IPsec tunnel information, such as tunnel identification and pass phrase.
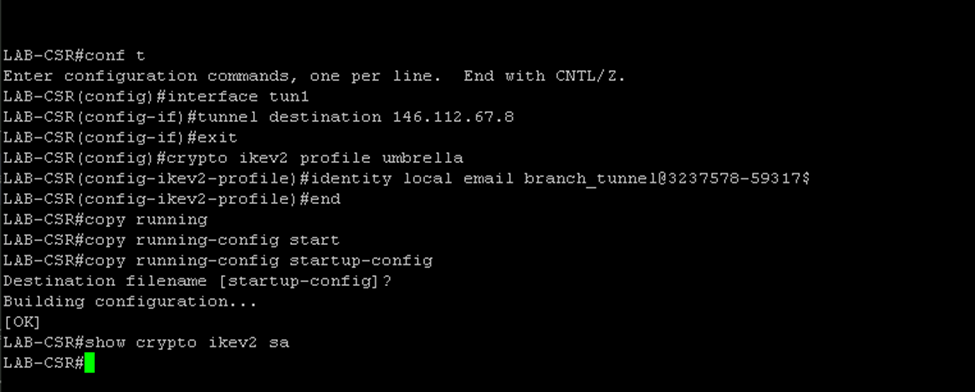
Here we will configure the tunnel destination and our tunnel identity into our CSR device.
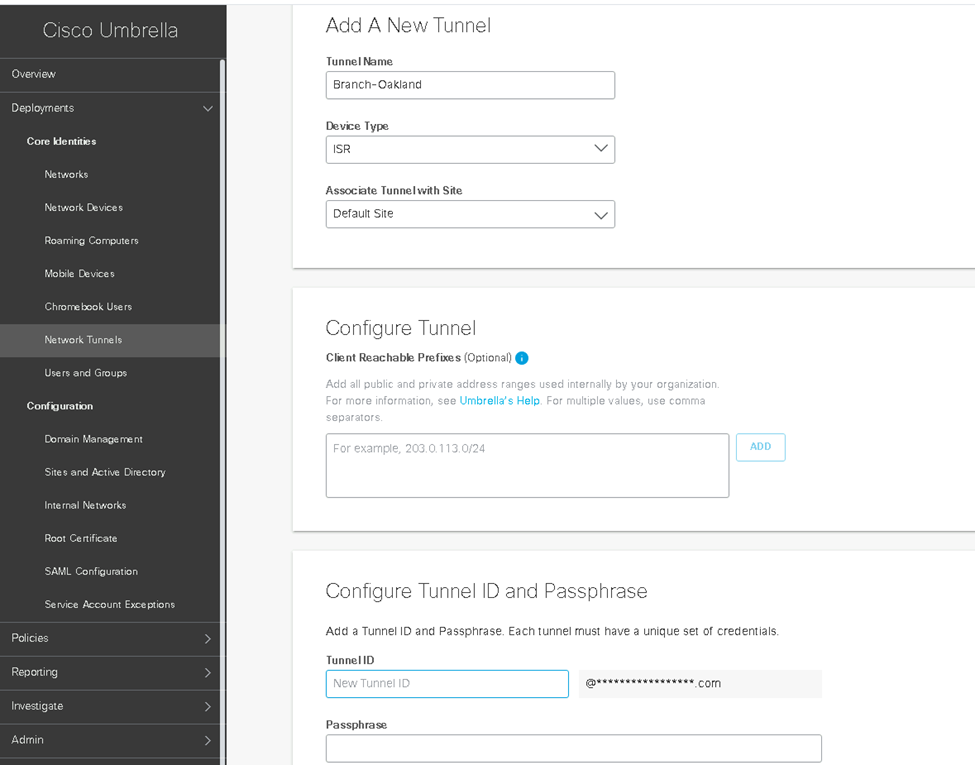
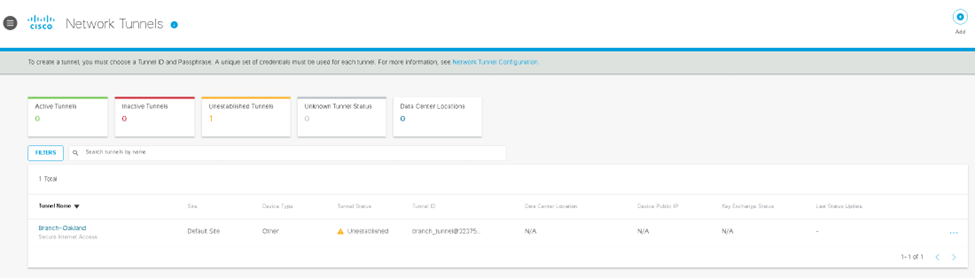
Here we will configure the tunnel destination and our tunnel identity into our CSR device.
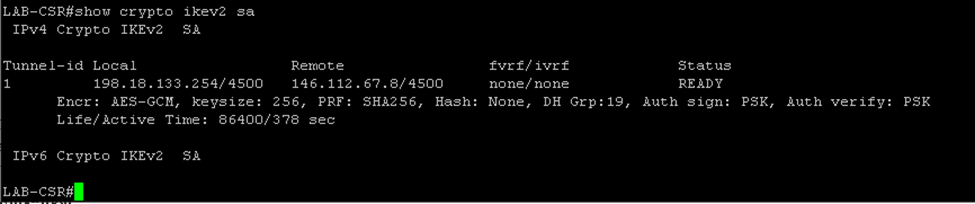
I bounced the tunnel and waited…Finally the tunnel came up.
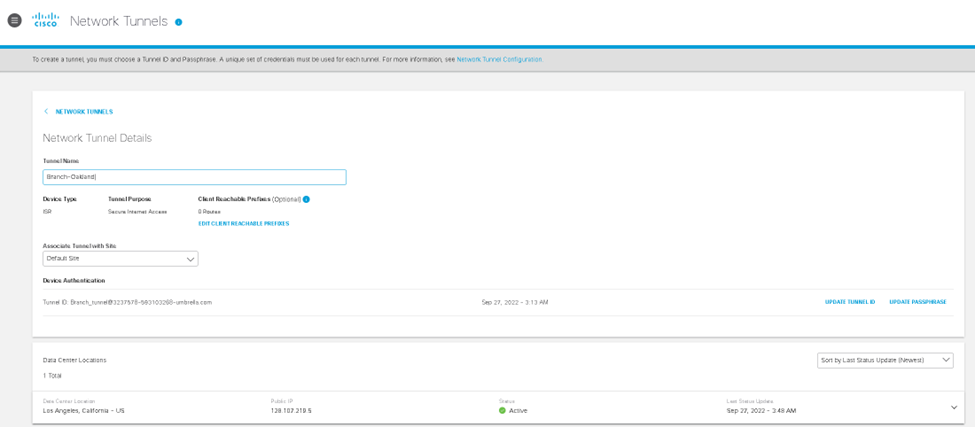
Umbrella Dashboard checks out!
Our next move once we’ve setup the IPsec tunnel between Umbrella and our device is to start configuring firewall policies. With these policies we can allow and restrict based on layer 3, layer 4 and layer 7. We are greeted with a default policy that allows all traffic.
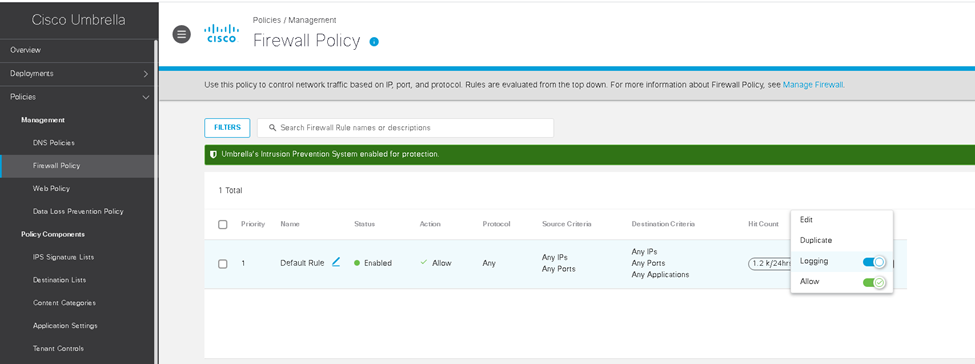
I wrote a policy to block access to a specific IP address within our location. Enabled logging and the rule itself.
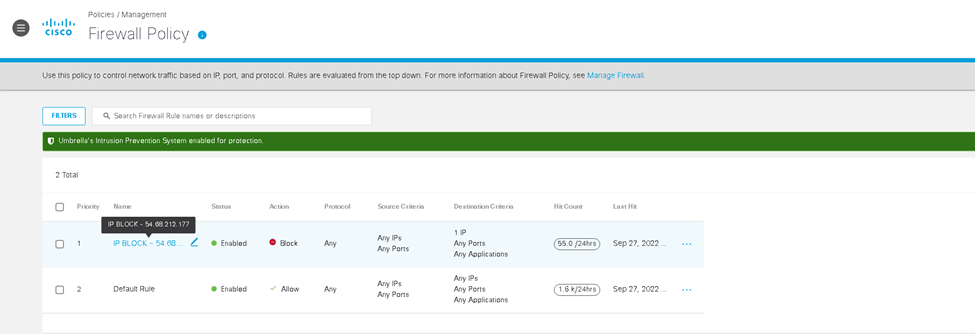
Proceeded to tested access but was denied due to our new rule. As the logs show we hit our rule. We can review the logs and see that our traffic is identified by the tunnel name we used earlier.
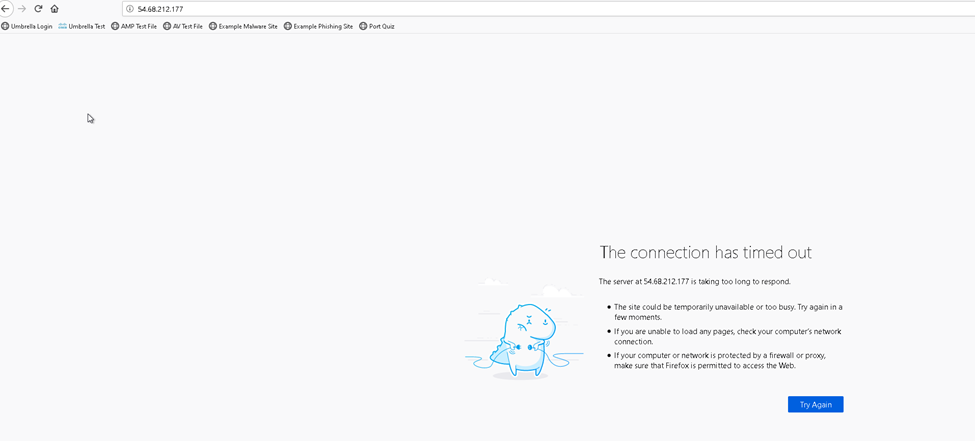
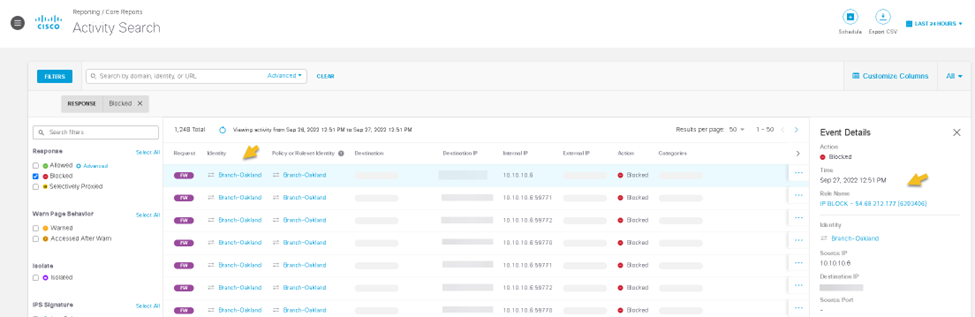
From here we can continue to leverage much more, such as stopping users from using applications. We can write policies to police applications that we do not wish on our networks like bit torrents.
As always if you have any questions on getting Cisco Umbrella Cloud Delivered Firewall set up for you and your business and would like to schedule a free consultation with us, please reach out to us at sales@lookingpoint.com and we’ll be happy to help!
Pablo Mirsoian, Network Engineer




