<Insert Creative/Witty/Charming Intro Here>.
How to Setup Anyconnect Remote Access VPN w/ Cisco FMC and FTD Firewalls, utilizing ISE & Duo 2FA for authentication and authorization, that’s a mouthful, isn’t it? For those who aren’t sure what I’m talking about, the goal of this blog is to pass along what I learned getting Anyconnect remote access VPN working with ISE and Duo 2FA for authentication/authorization.
I will quickly run through how we got it setup and hopefully will aid you with your own deployment. To recap, once this is implemented users will be able to VPN to their company, provide their AD credentials and get a push confirm request from Duo 2FA on their phones. If valid credentials are provided and the Duo push accepted the user would be allowed to gain access to the company’s networks. Obviously, anyone who doesn’t provide valid credentials and 2FA approval will be rejected.
This blog assumes you’ve got ISE configured to some extent and that AD identity sources are also already setup. It also assumes you’ve got more than a cursory understanding of Cisco’s FMC and FTD security products and topologies. Some tasks will be purposefully kept brief as some general understanding is assumed and will not be expanded on.
Required Components:
- FMC – Central Software used to manage the FTD Firewalls. Either VM or appliance based.
- FTD – Firewall(s) managed by FMC.
- Duo Account w/ Web Access – Duo account w/ valid licenses required.
- Duo Client Installed on Smart Phone
- Duo Proxy Server – Customer hosted windows server which runs Duo Proxy software. This server will send the actual request to Duo cloud servers for push notification to user.
- ISE w/ A.D. Identity Sources – Used to verify identity of a user.
Expected Remote Access Authentication/Authorization Flow Once Configured:
- User uses Anyconnect client and connects to businesses VPN host address from home.
- User is prompted for and enters username/password into presented fields.
- FTD device forwards received credentials to configured ISE Authentication Server group, which was defined under the remote access VPN Connection Profile section when setting up VPN in FMC.
- ISE receives the RADIUS request and gets triggered on a policy set we defined for VPN traffic, we’ve defined to match on device type. If matched to the VPN policy set the Authentication Policy will send request to Duo Proxy Server.
- Duo Proxy Server receives request from ISE server which in turn queries AD server for user authentication and sends request to Duo cloud to initiate Duo Push.
- User receives Duo Push on phone and presses ‘approve’. *user must be registered first*
- Access Accept is received on ISE from Dou cloud and proceeds through Policy set to the Authorization Policy.
- Authorization policy has a condition configured which verifies AD user group and the device type was ‘FIREWALL’. If these conditions are met access is permitted.
The above example doesn’t provide granular authorization for different groups but hopefully you’re getting some idea as to the flexible nature of the conditional approach to ISE policy sets.
Duo Admin Panel Dashboard
Before we can really get going with FMC/ISE VPN/policy changes we’ll want to get the required components setup. This means setting up an Application in the Duo Dashboard, recording the Application specific details and including those details in the config file (.ini file) on the Duo Proxy Server. I will briefly walk through these steps but for detailed instructions please visit https://duo.com/docs/cisco-firepower.
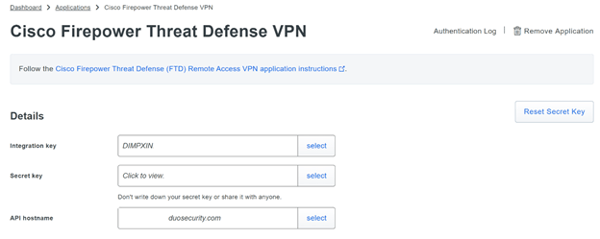
Once you have access to the Duo Dashboard, go to ‘Applications’ and add a new application called ‘Cisco Firepower Threat Defense VPN’. Take note of the Integration/Secret Key & API Hostname, these values will need to be entered in the Duo Proxy server configuration file. Follow the link above for more details about configuration options in the Duo Dashboard. With the above defined, next we’ll want to go to the Duo Proxy Server and get that setup.
Duo Proxy Server
Again, this write up does not dive into details on how to setup every single component but rather assumes the reader is familiar enough to setup the Duo Proxy server. Please refer to this document for assistance getting Duo Proxy Server configured.
https://duo.com/docs/cisco-firepower#install-the-duo-authentication-proxy.
The Duo Configuration file has sections to input the A.D. Domain Controller IP and connection details, which will be used to lookup user details for AD authentication. In addition, there will be a section in the config file reserved for the Duo cloud details (this is where you paste in the keys and API address you recorded earlier when setting up the Duo Dashboard).
This configuration section is pretty straight forward and I suggest you consult the above link if you’re not sure what you should be putting in the configuration file. Please make sure you’re either using administrator account to edit the file and take a backup.
😊 If you get stuck, we offer project support, blocks of hours, and even have managed service offerings which you can leverage for support in this and many other areas. Please email Michael@lookingpoint.com if you’d like me to put you in contact with a knowledgeable account manager. Or just email to say, “Hi”. 😊
FMC
First, you’ll want to setup remote access VPN configuration within FMC, this is done in a traditional manner which I will not dive into during this write up. Please follow this link for instructions on getting basic remote access VPN setup (with local or Windows NPS radius authentication). https://www.cisco.com/c/en/us/td/docs/security/firepower/630/configuration/guide/fpmc-config-guide-v63/firepower_threat_defense_remote_access_vpns.html#concept_gbn_jm2_2hb
It’s a good idea to get basic VPN working (without ISE/Duo) and tested before trying to implement the ISE/Duo components. Use FTD local usernames used until ready to proceed with full ISE/Duo component. You can refer to the Duo documentation for additional support here (https://duo.com/docs/cisco-firepower).
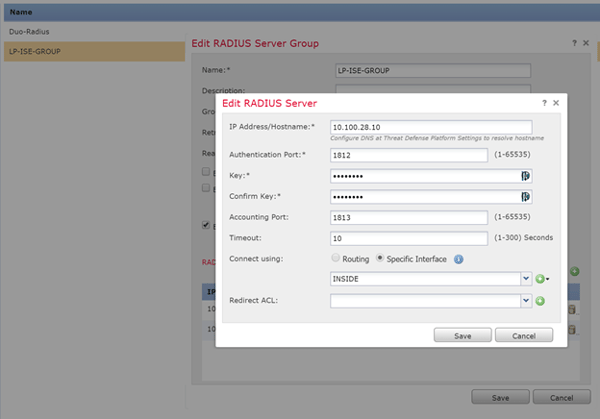
Once VPN with local usernames are working you’ll want to define a ISE RADIUS Server Group in FMC. Be sure to list each ISE PSN you’ll leverage as well as include the RADIUS Shared Secret you plan to use between FMC and ISE (to be configured on ISE’s Network Device entry for FTD, expanded on below).
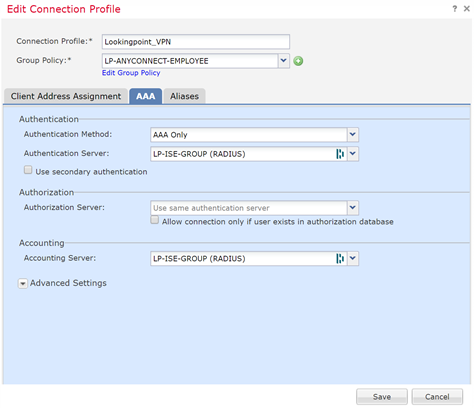
After the above is in place, the only change from a stock remote access VPN config will be to the ‘Authentication Method’ selection and will encompass changing the authentication server to the ISE server group we just defined. Please note the ‘Authentication Method’ section in the image below shows the ISE Authentication Group. I’ll revisit this near the end of the document once you’re ready to ‘turn on’ the ISE/Duo AAA function. For now, you can leave it local based.
ISE
At this point I will focus on the Policy Sets and the Authentication / Authorization Profiles that constitute its policies. This is where it all comes together, ISE receives the RADIUS access-request from the FTD device (along with your credential details). ISE first will run through the configured Policy Sets to try and find one that conditional matches. If a match is found it proceeds in predictable fashion down the AAA functions within that policy set.
ISE - Define External Identity Sources:
First, you’ll want to define the RADIUS TOKEN Identity Source, basically you’re telling ISE about the Duo Proxy Server, this Identity Source will be used in the Authorization Policy referenced in the Policy Set. It should look something like this:
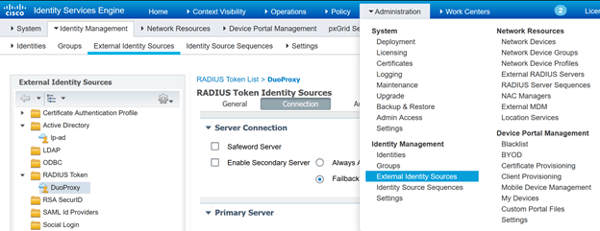
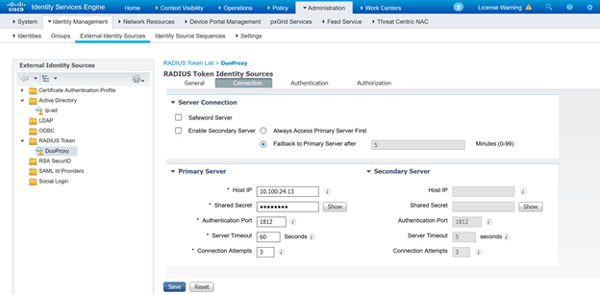
ISE - Define Devices w/ Specific Device Type and w/ RADIUS Shared Secret:
You’ll need to define the FTD network devices in ISE under ADMINISTRATION>NETWORK DEVICES. If it’s not already added, add your FTD device(s) to the device list and be sure to assign a device type and RADIUS secret key. The device type is a label which will be used to process requests from the FTD device. The RADIUS secret string will be configured in ISE under the device as well as on the FMC VPN configuration when defining the Authentication Server groups. Please see image below for reference, please follow Cisco’s documentation for defining new device type if one is required.
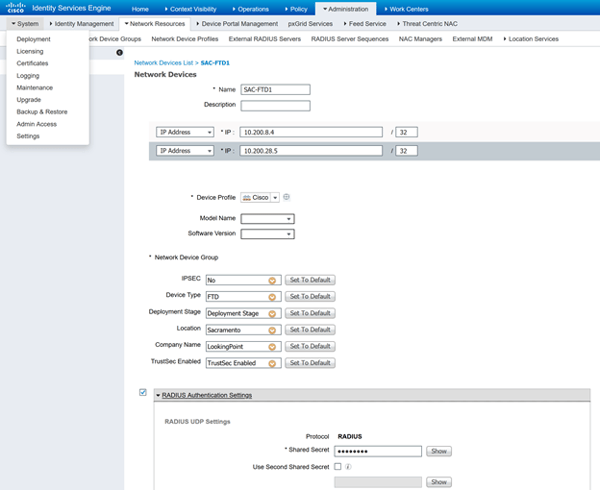
ISE - Define Allowed Protocols:
Next, the policy set will be configured to match access-requests sent from a certain device type and the type of authentication protocol used. In our case, we will be matching on “FIREWALL” device type and the allowed protocol will be PAP/ASCII since the credentials will be received as text.
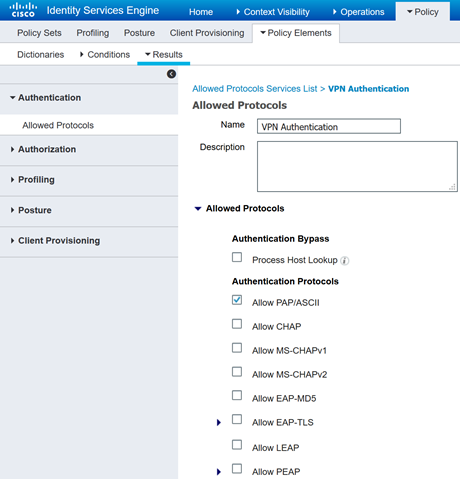
ISE – Policy Set (Bringing it all Together):
Lastly, we’ll put it all together, first we’ll define a new policy set, I’m calling it ‘DUO VPN Access’. I’ve listed the Policy Set Line below, the condition was defined in the condition library and only shows a description of the condition, for your reference it’s matching on device type FIREWALL (see 2nd screenshot). The Allowed Protocol field references ‘VPN Authentication’ allowed protocol object which we defined earlier as being text (PAP/ASCII).
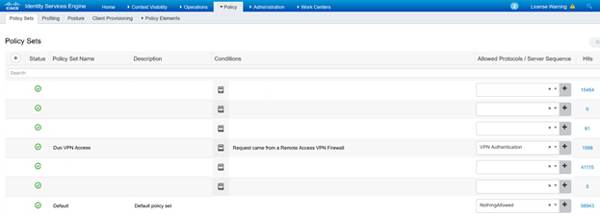
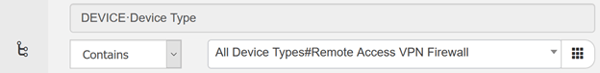
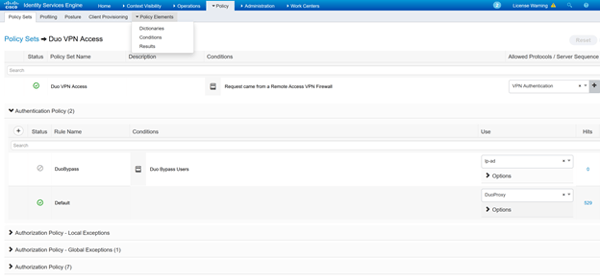
Drilling into the Policy Set, we see the Authentication Policy is defined as being ‘DuoProxy’, aka the Duo Proxy Server. Assuming the policy got to this part, the ASCII creds supplied by FTD will be sent to the Duo Proxy server, it in turn will check with the defined AD server to authenticate the user, if it passes AD authentication the Duo Proxy server will forward another request to the Duo cloud to initiate the Duo push to your phone. If you ‘accept’ the push, Duo Cloud will send the Duo Proxy server the accept message which in turn will return an access-accept message to ISE, thus fulfilling the Authentication Policy section of the policy set.
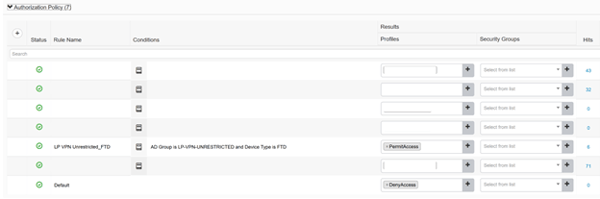
Next, and lastly, the Authorization Policy is pretty straight forward, it allows anyone from AD Group ‘LP-VPN-UNRESTRICTED’ coming from FTD to have full access. Notice the implicit deny at the end?
TESTING
It’s finally time to test, let’s fire up an external hotspot and give it a shot! Anyconnect to the public IP address you’ve selected for VPN. You should be presented with Anyconnect prompt for Username and Password. Enter your username and password and cross your fingers. If all goes well you should get a notification on your phone from Duo. Press accept, if you have any problems getting your duo push before timeout you may need to adjust the timeout value in FMC to 60 seconds to give you enough time to accept before timeout.
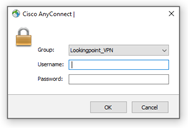
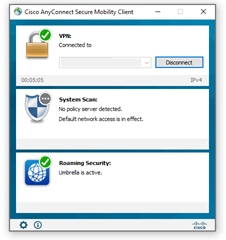
Success! Buy a lottery ticket!
Here’s what we see in the ISE Radius Logs, a resounding success!
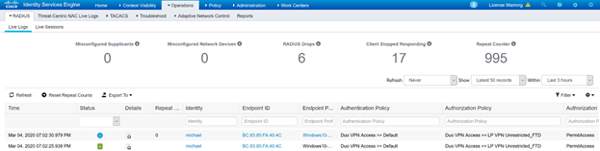
I hope you enjoyed this and found value. If you’re still banging your head against the wall email me at michael@lookingpoint.com and I’ll put you in contact with someone who can discuss our multitude of support options and services, let us take the burden off you!
Michael Lorincz, Network Engineer




