What is it? Panorama is a centralized management system from Palo Alto Networks. Which of course manages Palo Alto Firewalls. It uses templates to push configuration to each or multiple firewalls. Which you probably already know if you got one. But the question is how it is being used.
Templates contains the configuration for everything in the Network Tab and Device Tab.
Template Stacks are multiple templates combine.
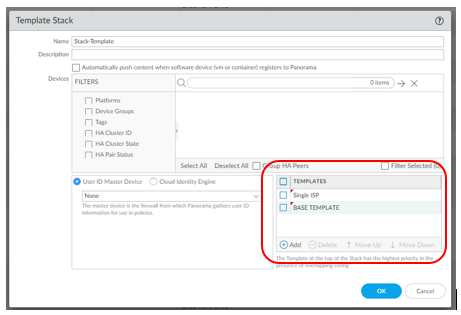
There are multiple ways in designing your templates.
- You can have a single template for each firewalls (which is the easiest way to manage them). No planning is required.
- You can have a template stack with multiple templates. Which requires some planning depending on your network topologies.
Planning for templates and template stacks.
How should you plan?
- If you choose option 1, then you only have 1 template per firewall. Simple and easy.
- If you choose option 2, then you need to decide what you want to standardize. Which type of configurations and network topology for which template? This all varies on your requirement. This will be the bulk of this conversation.
I recommend starting with a base template, which palo alto calls a global template, which should have all the same configurations for all your firewalls. Examples are Administrators, Log Settings, Server Profiles (SNMP Traps, Syslog, TACACS+, Radius) but not limited to those. It all depends on your configuration. Spend some time looking into it, and you can also make changes afterwards.
The next templates require some planning. Because this varies depending on how many different Network topologies that you have and how you want to design it. You can create a device template specifically for each firewall and add it to the stack template. You just created some standardization. But what if you have multiple different network topologies? For example, some firewalls are HA and some are not; Some firewalls have a single ISP and some have multiple ISPs, the list goes on. If you only have a couple firewalls in a small network topology, then it’s not much of a pain. But what if you have 20 firewalls in that type of topology and you have more sites coming up? This is where you must decide. Deal with the pain now or deal with it later. Either way, you’ll still need to configure it.
Creating more standard templates makes life easier in this scenario. I’ve created some standard templates below.
- HA Template – HA configuration. (Different firewall models have different ports. If you have different models, you’ll want to create additional templates per model.)
- Single ISP template – Interface configuration with variables. Routes configuration.
- Dual ISP template – Same configuration as the Single ISP template but with more ISP.
- Device templates – Specific configurations for firewalls. (VPNs, sub-interfaces).
Now I mentioned Variables on the templates above. Template Variables are configuration components for the template. Every firewall usually has different IP addresses. So, this makes it easier when implementing a new firewall. Examples are IP addresses for interfaces and HA settings. Variables names must start with $ sign. Example below.
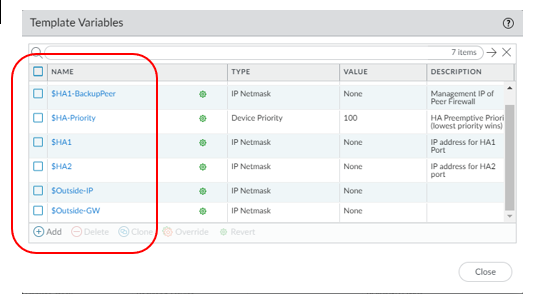
You’ll need to export the variable from the stack template, which is a CSV file. Input the data for your variable, save it and import it back into Panorama. Commit to Panorama before pushing it to the device.
How you stack these templates are also important. The template on top has highest priority, and it will override any templates below if there are any matching configurations.
Example: Top template has an interface with Ip address 1.1.1.1 and a template below it has the same interface with Ip address 2.2.2.2. That interface will get an ip address of 1.1.1.1.
With my templates, it will be stacked in the order below.
- Device template
- Single ISP template
- HA template
- Base template
With these standard templates in place, my integration steps for a new firewall are below.
- Added Firewall to Panorama
- Create or add firewall to device group for policies.
- Clone Single ISP template and make it a device template with the additional configurations.
- Create a stack template and add the require templates.
- Export variables CSV and input data.
- Import variables.
- Commit and push to device.
Keep in mind that these template designs all vary in so many ways. It all depends on your plans and desire output. It’s probably best to plan something now before you add too many firewalls to your plate.
Troubleshooting notes.
I ran into some commit errors on the template stack that I spent some time on, looking for the configuration. Best way to locate these configurations is start with the template stack instead of the individual template. Once you find it on the stack template, move your mouse over the green setting icon. It’ll tell you which template it is on. If you can’t find it there, then look at the device configuration.
I also had some issues with the variables. Some ip-netmask variable types require a CIDR input and some just require IP address. Importing and committing to Panorama doesn’t give an error, but when you push to the device, that’s when you’ll see the error.
I hope this had some good insight for you. Thank you for reading.
As always if you have any questions on Palo Alto Networks Panorama for you and your business and would like to schedule a free consultation with us, please reach out to us at sales@lookingpoint.com and we’ll be happy to help!
Kenny Wong, Engineer




