Introduction
This will be the final installment in this NSLOOKUP Primer series. Last time, I talked about MX & SPF TXT records here, but I didn’t touch on DMARC & DKIM TXT records which are also highly encouraged to help add additional layers of security to your email domain.
Definition
DKIM = DomainKeys Identified Mail
DKIM helps detect forged (spoofed) email addresses by adding a cryptographic digital signature linked to a domain name and publishing a public key in DNS that mail recipients can compare to check for authenticity.
DMARC = Domain-based Message Authentication, Reporting and Conformance
A DMARC is designed to protect against spoofing by extending SPF & DKIM. A policy is published in DNS which specifies what mechanisms are used (SPF, DKIM, or both) by an email sender and suggests what a recipient should do with a message that fails a test of the specified mechanisms.
Information
DKIM
Even though DKIM is ultimately a DNS-published key, different email providers have different methods of enabling DKIM. The official documentation suggests using _domainkey.[domain], however I’m going to focus on Microsoft’s Exchange Online due to how common it is. When you configure DKIM for Exchange Online, you’re asked to create CNAME entries in your domain’s DNS to point to TXT entries in Microsoft’s DNS. This allows you to request a DKIM key rotation from your admin portal without having to touch your own DNS. The format of the entries are like below, where [domain] is the domain you’re checking, although I’m assuming .com for the first level.
CNAME = selector1._domainkey.[domain].com => selector1-[domain]-com._domainkey.[domain].onmicrosoft.com
CNAME = selector2. _domainkey.[domain].com => selector2-[domain]-com._domainkey.[domain].onmicrosoft.com
So let’s follow take a look using cisco.com as our example to look up a DKIM entry.
- Select an external DNS server (I don’t see DKIM entries set on internal DNS servers)
- Set type to CNAME
- Use the format above to lookup a domain that’s utilizing MS Exchange Online DKIM
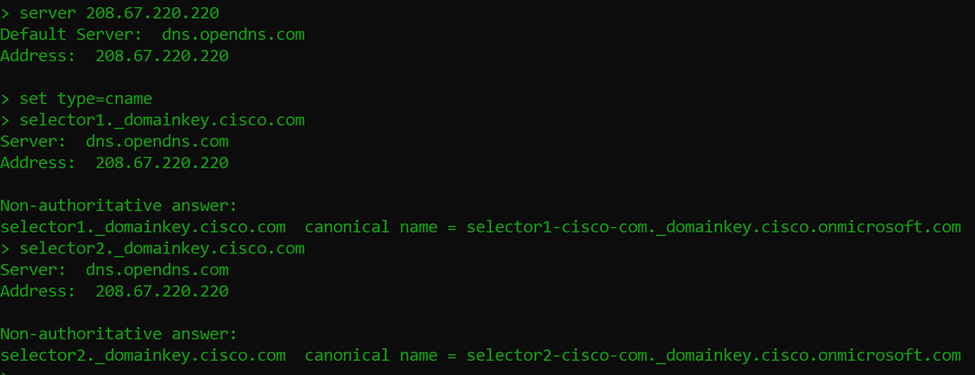
-
-
- Follow the trail to the Microsoft text record
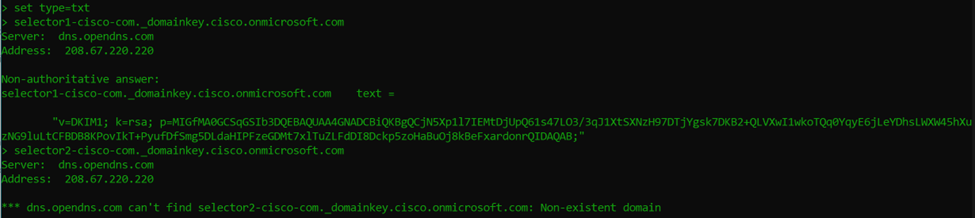
If we break down the record we see, it specifies the following:
v=DKIM1 – This is the version of DKIM
k=rsa - This is the key type
p=[public key] – This is the public key data in base64
Although this record is a good representation of what I usually see, there are more options available in a DKIM record. More information on other syntax can be found at the RFC section 3.6.1 here. What we can see from our results is that the selector1 record has a DKIM key, but not selector2 which I am assuming is because it’s there as a “just-in-case” or “for future use”.
DMARC
Now that we’ve looked up a DKIM record (and an SPF record in a previous post), let’s take a look at a DMARC record. Typically, DMARC records are a DNS TXT record with the format _dmarc.[domain].com. To keep consistent with our previous example, let’s look at _dmarc.cisco.com.
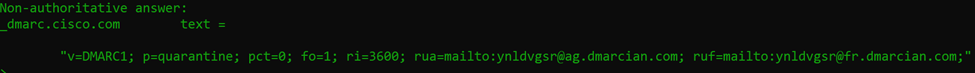
Let’s break down each of the tags in the TXT record:
v=DMARC1 – this is the version of DMARC (at this time it’s always DMARC1)
p=quarantine – this is the policy and can be none, quarantine, or reject
pct=0 – this is the percentage of messages that the policy should be applied to (0 – 100)
fo=1 – this is the failure reporting options (paired with ruf) and can be 0, 1, d, or s
0 = Generate a failure report if all auth mechanisms fail to pass
1 = Generate a failure report if any auth mechanisms return something not pass
d = Generate a DKIM failure report if message signature failed
s = Generate an SPF failure report if SPF evaluation failed
ri=3600 – this is the interval between aggregate reports in seconds
rua=mailto:[address] – comma separated list of email addresses to receive aggregate feedback
ruf=mailto:[address] – comma separated list of email addresses to receive failure information
It’s not in our example, but there’s another tag, “sp=” which is a subdomain policy that will allow you to set a different policy for email sent from subdomains. It’s also important to note that the tags must be in a specific order for it to work properly. For more information on the format of DMARC records, check out RFC 7489 section 6.3 here.
So I’m not sure if you caught that, but based on the DMARC record above, Cisco is asking mail servers receiving mail from them to quarantine 0% of their email from the cisco.com domain. Now they’re a big company, so they may have other DMARC records for any number of subdomains, but that’s how I’m interpreting that record.
Also worth noting is that if you don’t have SPF and/or DKIM already configured, DMARC won’t do anything. It should be thought of as an extension of those methods to define the policy you’d like mail recipient servers to take when mail doesn’t pass the checks. **NOTE: these policies aren’t forced, they’re requested.
Conclusion
Well hopefully this was a fun exercise you were able to follow along with to learn a little more about NSLOOKUP and DNS-based mail security at the same time. As I conclude my NSLOOKUP primer series, I dream of people reading over these 3 articles and feeling more comfortable with the tool as something quick and useful that’s built in to most operating systems for verifying DNS entries both internal and external.
- Follow the trail to the Microsoft text record
-
-
It just so happens that LookingPoint offers multiple IT services if you’re interested. Want more information, give us a call! Please reach out to us at sales@lookingpoint.com and we’ll be happy to help!
Ryan Alibrando, Managed Services Team Lead




