Today more and more businesses are focused on application security and visibility. With expected exponential growth in online devices - from 15B today to an expected 500B by 2030, securing those devices has never been more important. Today’s rapidly evolving business models reflect trends like hybrid cloud, mobility and BYOD, meaning the traditional network perimeter has largely dissolved. The ability to protect the endpoint and the extended network is an increasing necessity.
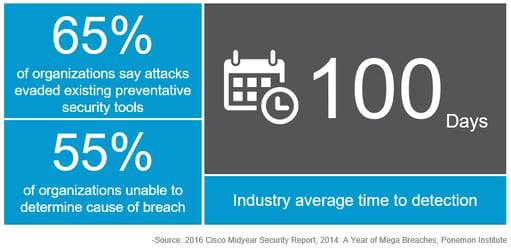
Organizations are under the constant threat of cyber-attack, and security breaches are happening every day. Today’s attackers are creating advanced malware that is quickly evolving and more sophisticated than ever. Traditional defenses, such as firewalls or anti-virus, no longer protect against the dynamic advanced malware attacks being used to exfiltrate data from your endpoints. It’s no longer a question of “if” malware can breach your defenses to compromise your endpoints, it a question of “when”. The only way to mitigate today’s security threats is to take a platform approach protecting your environment. Secure the perimeter, protect the endpoint regardless of location, and ensure visibility throughout the digital landscape.
“When you see a single ant on your kitchen counter, you know he’s not alone. Somewhere in the cracks and crevices of your kitchen appliances, hidden from your view, is a multifaceted, coordinated army of ants waiting to strike. This is analogous to malware. You may see one piece of malware here or there on your system, but it’s just the beginning. You need to see where else that malware is hiding and how it’s connected and working together. You need to uncover all of the ants and eliminate the army in hiding if you really hope to fix the entire problem.” –John Dominguez, Cisco Product Marketing Manager, Advanced Malware Protection
To protect your environment against today’s threats you need an endpoint security solution that includes these 9 “must haves”:
- Cloud or on-premises deployment options, across multiple operating systems
- Prevention capabilities
- Integrated sandboxing capabilities
- Continuous monitoring and reporting
- Rapid time to detection
- Agentless detection
- Easy, streamlined management interface for efficient decision-making
- Simple, automated response
- Part of a larger integrated security architecture
To be effective against today’s threats, your endpoint security solution needs to be as multidimensional and dynamic as the advanced malware attackers are creating. More than a decade ago, the standard for network visibility was to use invasive network prevention, or “point-in-time”, scanning tools. The new models to secure endpoints has transformed that traditional “point-in-time” approach into a continuous approach. This new continuous approach model continuously monitors, detects and responds to threats if they breach your network. It delivers visibility and allows security teams to quickly and effectively contain and remediate breaches without disrupting end users.
A true continuous approach model should address the most important security questions:
What was the method of entry and what systems were affected?
Your endpoint security solution should provide deep analytics with device trajectory, showing the systems affected by malware, including patient zero and the root causes associated with a potential compromise.
What did the threat do?
File analysis should provide detailed information about malware including file behavior, original file name, malware executing screenshots, and sample packet captures.
Can my organization stop the threat and eliminate root cause and prevent it from happening again?
You need an endpoint security solution that can effectively stop the spread of malware and malware-related activities. Your solution should also automatically remediate systems without a full scan.
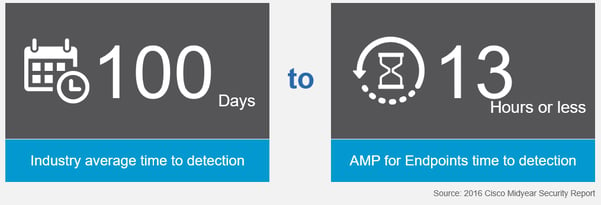
Cisco Advanced Malware Protection (AMP) for Endpoints is a cloud-managed endpoint security solution that provides the visibility, context, and control to not only prevent breaches, but also rapidly detect, contain, and remediate threats if they evade front-line defenses and get inside.
- Prevent: Strengthen defenses using the best global threat intelligence and block malware in real time.
- Monitor and detect: Continuously monitor and record all file activity to quickly detect stealthy malware.
- Respond: Accelerate investigations and automatically remediate malware across PCs, Macs, Linux, and mobile devices.
AMP for Endpoints also protects mobile devices. Visibility extending to mobile devices allows you to quickly understand what devices have been infected and which applications launched malware into the system. The ability to enforce which applications can be used on mobile devices accessing corporate resources allows you to remediate attacks, and keep your network secure. Built on real-time threat intelligence and dynamic malware analytics, AMP for Endpoints provides organizations the benefits of:
- 1.5 million incoming malware samples per day
- 1.6 million global sensors
- 100 terabytes of data per day
- 13 billion web requests
- Team of engineers, technicians, and researchers
- 24-hour operations
Learn more about endpoint protection here.
Written By: Eden Penman, LookingPoint Marketing Manager



