Firepower FTD Remote Access VPN SSO using SAML and Azure AD, with Azure AD Conditional Access to Duo 2FA, and Cisco ISE for Authorization and Group Policy Assignment
There are multiple components to this solution, and while there are a few different approaches to accomplish the end goal, I wanted to focus on a solution that didn’t require an onsite Duo Authentication Proxy server. This blog will focus on using Cisco Secure Client (Formally known as Cisco Anyconnect) to establish a remote access VPN connection with a Cisco Secure Firewall (FTD) and have user authentication sent to Microsoft Azure Active Directory (AAD) via SAML request, which in turn would authenticate users using its local user store.
In addition, Azure would kick off a 2-Factor Authentication request against Duo using an Azure Conditional Access policy. If properly authenticated with AAD/Duo, Authorization would then be sent to on-prem ISE server for Authorization. If successfully matching policy conditions, the ISE Authorization Profile will return a Cisco ASA/FTD VSA which the firewall will use to assign the VPN user to a specific Group Policy. The Group Policy would define specific details for that VPN connection (restrictions through ACL, split tunnels, client modules, etc). This is helpful if you’d like to differentiate access based on the user’s group memberships.
You may only have one user type in your organization that needs VPN access (employees with full access), and this guide can still be used for these cases, but you may find this guide especially helpful if you need to restrict access based on different AD groups. You can achieve this using Group Policies on the FTD based on authorization results from ISE, which can be leveraged to verify the user/group and return an attribute value to the FTD. This gives you the ability to differentiate different access rights based on the AD group the user belongs to. Our VPN setup separates ‘Employees’ from ‘Contractors’ and grants restricted access to ‘Contractor’ users connecting by assigning the ‘Contractor’ Group Policy for which they are authorized.
This blog will assume you already have some familiarity w/ configuring remote access VPN on Cisco Firepower devices through the FMC, as well as some familiarity defining ‘Enterprise Applications’ in Azure AD portal and the Duo Admin Portal. Lastly, having a basic understanding of ISE policy structure, conditions, and Authorization Profiles is also helpful. I’ll keep things rather high level but if you get stuck, please drop a comment below and I’ll do my best to answer.
Solution Components:
 Cisco Secure Client (Formally Anyconnect) – This is the client the end user will use to setup the remote access VPN connection. It supports addon modules such as the Umbrella Roaming Security Module for roaming security, and ISE Posture Module for posture assessment.
Cisco Secure Client (Formally Anyconnect) – This is the client the end user will use to setup the remote access VPN connection. It supports addon modules such as the Umbrella Roaming Security Module for roaming security, and ISE Posture Module for posture assessment. Cisco Secure Firewall (FTD) – This is the firewall terminating the VPN connection. It will also send the SAML requests to Azure AD for Authentication, which in turn will utilize ‘Conditional Access’ policies in Azure to kick 2FA to Duo. If successful, it will then send Authorization request to On-Prem ISE server. *Please note, you’ll need to use Firepower 6.7 and later to have SAML option. *
Cisco Secure Firewall (FTD) – This is the firewall terminating the VPN connection. It will also send the SAML requests to Azure AD for Authentication, which in turn will utilize ‘Conditional Access’ policies in Azure to kick 2FA to Duo. If successful, it will then send Authorization request to On-Prem ISE server. *Please note, you’ll need to use Firepower 6.7 and later to have SAML option. * Microsoft Azure Active Directory
Microsoft Azure Active Directory
-
- Users/Groups – These users and their group memberships would be used with the initial SAML request for Authentication, and in the Azure AD Conditional Access (CA) policies. Many organizations sync on-prem AD with Azure AD using Azure AD Connect
- Azure AD Conditional Access (CA) policies allow you to set policies that evaluate Azure Active Directory user access attempts to applications and grant access only when the access request satisfies specified requirements e.g., user group membership, geolocation of the access device, or successful multifactor authentication (we’ll be creating a Duo Condition in our CA Policy).
- Enterprise Applications – These are the ‘Apps’ you define in Azure, each will have its own Idp Entity ID and published certificate we’ll need to import into the FTD.
-
 Duo 2FA – This is a popular service used for 2FA and SSO. The 2FA challenge will be initiated from Azure using Conditional Access policy our Azure Enterprise Apps will use.
Duo 2FA – This is a popular service used for 2FA and SSO. The 2FA challenge will be initiated from Azure using Conditional Access policy our Azure Enterprise Apps will use.
- Azure will Utilize Conditional Access policies as defined here
- This blog does not use the Duo Single Sign-On product. ‘Duo Single Sign-On’ is Duo’s cloud-hosted SAML 2.0 identity provider service. Which provides primary and Duo secondary authentication as the acting identity provider. We will use Azure AD as our Idp.
 Cisco Identity Services Engine (ISE) - ISE is a next-generation identity and access control policy platform that enables compliance. We’ll leverage ISE specifically for the 2nd ‘A’ in AAA, Authorization.
Cisco Identity Services Engine (ISE) - ISE is a next-generation identity and access control policy platform that enables compliance. We’ll leverage ISE specifically for the 2nd ‘A’ in AAA, Authorization.
- We’ll need to define a Policy Set to identify requests from the Firewall, as well as proper Authorization Policy/Profile. The end result should hopefully be a RADUIS access-accept with a customer attribute value returned to the FTD to be used for Group Policy assignment.
** Some Screenshots may be from miscellaneous online sources, so some object variables defined may differ from what I’m writing in the guide **
Expected Event Flow:
First, before I blast you with configuration steps, I will run through a high-level flow of how things are supposed to work once everything is setup. My goal is to provide some framework that can be referenced when reviewing the actual configuration aspects later in this blog.

- Client Connects to VPN Firewall using Cisco Secure Client. The FTD Firewall generates the SAML request and should be configured with the AAA Authentication Method Set to ‘SAML’ and Azure Authentication Server defined in the Connection Profile.
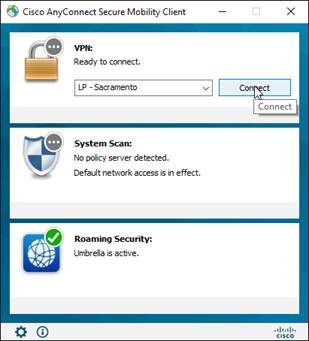
2. The Client sends SAML Request to Azure AD. Azure AD should be setup with a ‘Cisco Anyconnect’ Enterprise App defined along with a Conditional Access policy requiring Duo2FA.
3. Client will see a popup login prompt from Azure AD in VPN Client, they will be prompted for Azure credentials. Use fqdn like user@domain.com to login.
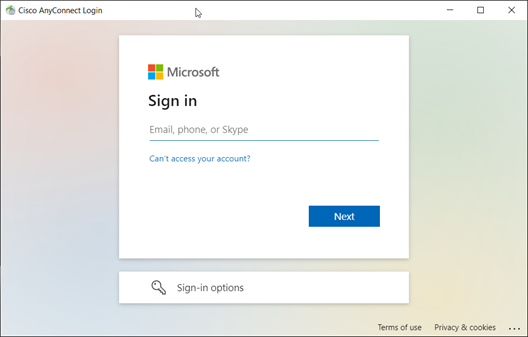
4. After the user is authenticated against the Azure AD user store, the Conditional Access Policy related to Duo2FA will be triggered. This will initiate the Duo 2FA Authentication Request for the Users/Groups defined in the Conditional Access policy.
5.Duo Push or SMS sent to Client Device Enrolled Duo User.
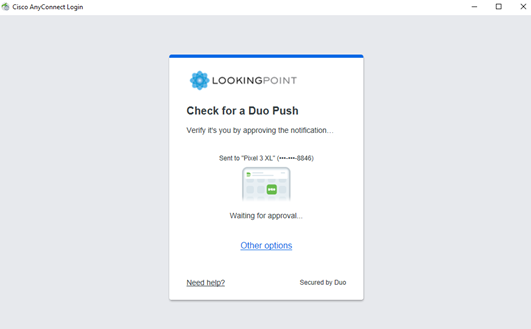
6. Approval from Duo Client Device Returned to Duo
7. Duo Success or Failure Returned to Azure Conditional Access policy, if successful, Conditional Access Policy Should ‘Grant Access’.
8. Azure AD returns the encoded SAML assertion to the Anyconnect client.
9. Client sends the SAML assertion to the FTD to wrap up the Authentication portion. Assuming both Azure credential and Duo 2FA passed.
10. Authorization request sent to ISE server per AAA defined in Connection Profile. A Policy Set should be created to identify VPN login authorization requests and properly authorize those requests and assign attributes to be used by the firewall (Group Policies).
11. ISE Receives the Authentication Request and matches the appropriate policies and sends the authorization radius-accept with custom attribute.
12. The FTD completes the VPN setup and applies the Group Policy for that User Group and downloads any related service modules, ACLs, and any other group specific configuration details.
13. Client user now has access!
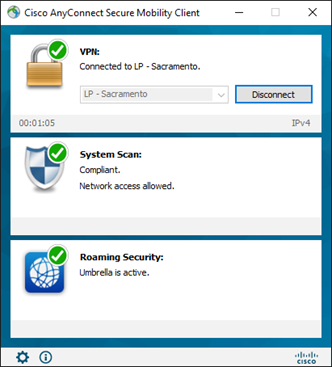
Authentication Configuration:
This section will discuss the Authentication with Azure and Duo pieces. The following section will specifically address the Authorization with ISE element. I won’t cover each step for the basic Remote Access VPN setup as I will assume you can setup a basic working RA instance using local or RADIUS authentication initially. There are tons of great resources online to walk you through the initial VPN setup. With that said, let’s dive in.
First, let’s Create ‘Anyconnect’ Azure Enterprise Application and Define FTD’s Azure SSO Server
First, we’ll get started in Azure portal, we’ll have to create a new ‘Enterprise Application’. In the Admin portal, navigate to the Azure AD à Enterprise Applications. Add a new Application and search for ‘Anyconnect’, then click ‘Create’.

Next, we’ll record the Login URL / Azure AD Identifier / and Logout URL generated for the Application by Navigating to the ‘Set up Single Sign On’ section under the Application Overview. Scroll down to section 4 and copy the three fields into a text file, we will refer to these when configuring the Azure SSO Server.

Download the Azure Identity Certificate under ‘Set up Single Sign On’ under section 3. Download the BASE64 Certificate. You will open this file and copy its contents when importing into the FTD.

From FMC, let’s get some configurations in place. We’ll define some URL object(s) and add the Azure Single Sign On Server to FMC.
In FMC, navigate to OBJECTS > URL, and create a URL which you intend to use for VPN. If you will have multiple sites, it’s best to create a single object with overrides as shown below. Common URLs would look something like https://access.yourcompany.com or https://vpn.yourcompany.com.

Next, in FMC, let’s add the certificate we downloaded from Azure and create the Azure Single Sign On Server.
Enroll Azure Certificate in In FMC – Navigate to OBJECT > PKI > CERT ENROLLEMENT and click ‘Add Cert Enrollment’. Next Pick a Name, select ‘manual enrollment, check the ‘CA Only’ checkbox as well as the ‘Skip Check for CA’ checkbox. Lastly, open the cert you downloaded from Azure and copy the contents to the ‘CA Certificate’ box and click save. I suggest creating a new certificate enrollment for each site and not using override here.
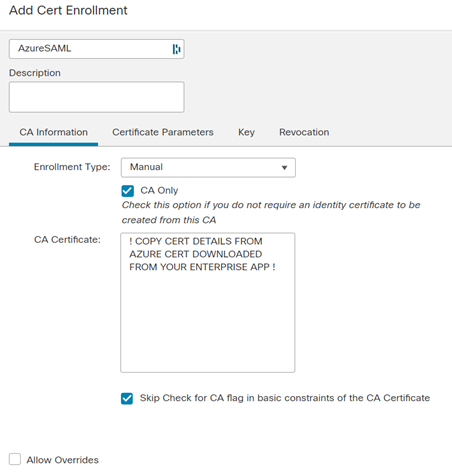
Now let’s push the Azure Certificate to the FTD device, in FMC, navigate to DEVICES > CERTIFICATES and click ‘ADD’. Select the FTD device, and under ‘Cert Enrollment’ select the ‘AzureSAML’ cert you added in the earlier step. It should now show up in your main cert store. Do this for each cert/site you defined earlier.

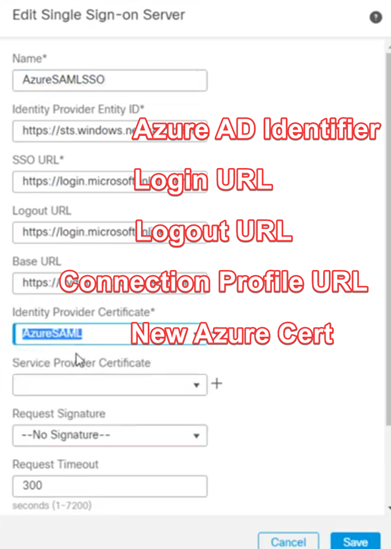
Next, we’ll create the ‘Azure Single Sign On’ Server in FMC, navigate to OBJECTS > AAA SERVER > Single Sign-On Server and click ‘Add Single Sign-On Server’. It’s possible to use ‘overrides’ here to define Authorization to Azure for multiple sites, I suggest creating a separate Anyconnect App in Azure for each site. Update the fields as I’ve summarized below, once complete click save.
- For the Idp Entity/SSO URL/Logout URL fields, please use the URLs you recorded from the SSO section of the Anyconnect App you created earlier in Azure.
- Reference the URL you defined earlier in the URL object. Might look something like ‘https://vpn.yourcompany.com’.
- Under ‘Identity Provider Certificate’ section, select the certificate you enrolled earlier.
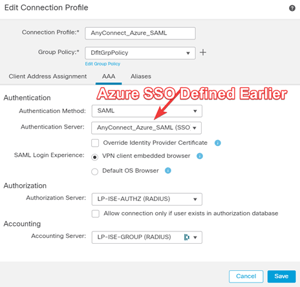
Finally, let’s update the FMC’s remote access configuration with new Authentication Server
You should have already created a working Connection Profile using RADIUS or Local Username for initial VPN connection, which we will now update to use the AzureSSO Single Sign On Server by changing the Authentication Method and selecting the new Authentication Server. We’ll edit the Group Policy section later under the Authorization section of this guide, there we’ll define the ACLs that will apply to the different type of User Groups (Employee, Contractor, etc).
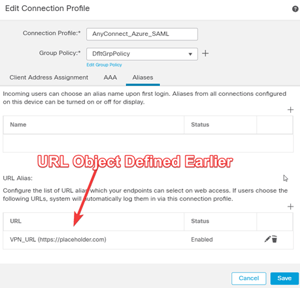
Edit the Connection Profile and Update the Authentication and Aliases sections.
Update Azure Anyconnect App w/ FTD Specific Meta Data
We’ll need to update the ‘Basis SAML Configuration’ section in the Azure Anyconnect App we created earlier, this provides Azure the details on where to send user AFTER authentication.
Navigate to the Single Sign On Section and edit #1, but first let’s grab some metadata from the FTD device. After you configure the Azure Connection profile, login to the FTD command line and run, “show saml metadata <CONNECTION_PROFILE_NAME>”. In my case, I would run “show saml metadata AnyConnect_Azure_SAML” since that’s the connection profile name I used, the screenshot below was taken from a different device and it used connection profile name Azure. Just be sure to use the connection profile you defined.
- Copy these three URLs and edit Azure Application SSO Section #1 and updated the fields with these URLs, only paste the ‘https’ portion (my screenshot was pulled from a different device, URLs may vary between my screenshots)


Save your work and let’s move onto the Duo component.
Let’s now complete the Azure to Duo Conditional Access Component.
As show in the flow from earlier, Azure AD will be responsible to send 2FA requests to Duo. It will leverage a conditional access policy for this piece. I’ll refer you to a guide published by Duo to get this implemented. The guide can be found HERE, the video found at that link is a great quick guide to getting Duo CA setup between Duo and Azure. No Need for me to re-invent the wheel 😊
There are some pre-requisites requirements you should be aware of.
- You’ll need an active Azure AD Premium P1 or P2 subscription including Conditional Access
- A designated Azure admin service account to use for authorizing the Duo application access.
To summarize the tasks outlined in the Duo Guide referenced
- Create the Duo Azure CA Application in Duo Portal (this will walk you through granting access to Azure from Duo)
- Create the Duo MFA Custom Control in Azure Portal
- Create and Apply a Duo Conditional Access Policy in Azure Portal. Be sure to apply to the Anyconnect cloud App you created in Azure earlier.
Authorization Configuration:
The Group Policy assigned by the FTD is determined through the Authorization stage, authorization requests are sent to the ISE appliance for policy matching and group policy assignment. ISE Authorization Policy will check the AD groups the user is a member of and if it matches the condition (belonging to a specific group) ISE will return an attribute defined in the corresponding Authorization Profile. The FTD will compare this attribute to its Group Policy list and assigns the proper Group Policy to the user based on group membership. This will grant the appropriate access and ensure the user connection adheres to the Group Policy defined (may define unique client modules, ACLs, etc).
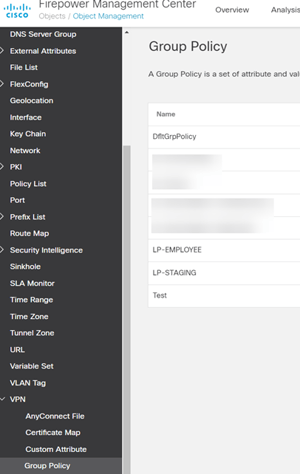
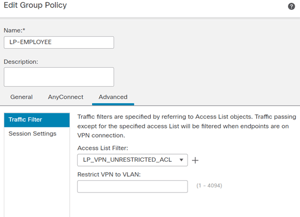
First, let’s define the Group Policies we think we’ll be issuing to users. In the example screenshot we’ve got a handful of Group Policies already defined. The main difference between them is the ‘VPN Filter’ ACL which is referenced. The Group Policy name is important to remember, as we will be defining these Group Policy names in the Authorization Profiles in ISE. ISE will return an attribute that is defined in the ISE AuthZ Profile, and it will match the group policy name that FTD should use. That referenced Group Policy will be used, regardless of what you initially selected as your group policy in the FTD VPN Connection Profile.
Once applied to a vpn connection (based on the returned attribute from ISE), the appropriate Group Policy will be used. In our case LP-EMPLOYEE will provide Unrestcited Access and LP-STAGING will provide restricted access to contractors who are assigned to the LP-CONTRACTOR AD group.

ISE Authorization Setup
You should hopefully have some idea on how to configure Policy Sets in ISE, I won’t go in depth on this topic but rather provide a bullet list and some example screen shots of the critical pieces.
- First, make sure the Firepower Network Device is defined in ISE, and assign a device type that can be referenced as a condition in a policy set (for example ‘Remote Access VPN Firewall’)
- Create the Authorization Profiles for each User Type, example shown below. The Authorization Profile will be referenced during policy matching, which will look at user group membership to identify which Authorization Profile to use.
- Be sure to check the ‘ASA VPN’ common task and type the FTD Group Policy name. A unique AuthZ Profile needs to be created for each type of user/group that will need to have a dynamic FTD Group Policy assigned. In our case, we’ll match on LP-EMPLOYEE and LP-CONTRACTOR AD groups.
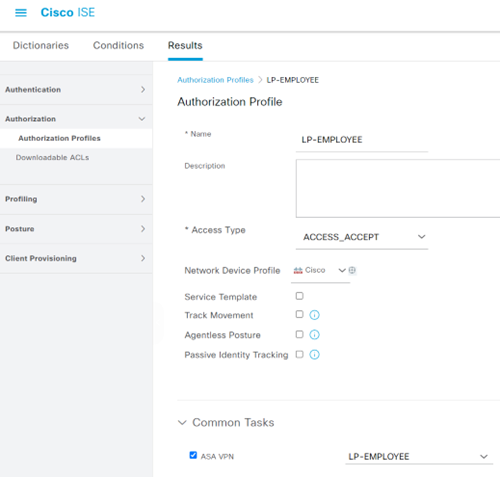
- Be sure to check the ‘ASA VPN’ common task and type the FTD Group Policy name. A unique AuthZ Profile needs to be created for each type of user/group that will need to have a dynamic FTD Group Policy assigned. In our case, we’ll match on LP-EMPLOYEE and LP-CONTRACTOR AD groups.
- Last, we’ll create the actual Policy Set and related Authorization Rules.
- For the Policy Set rule, we’ll match on requests coming from device types ‘Remote Access VPN Firewall’, make sure Radius Service-Type is set to ‘Authorize’ only, that way it skips the AuthC portion of the rule (we’re only using ISE for Authorization).

- The Authentication Policy piece will match the user to a specific group and if matched, will assign one of the Authorization Profiles we defined earlier. You’ll also want to have an implicit deny at the end.
- For the Policy Set rule, we’ll match on requests coming from device types ‘Remote Access VPN Firewall’, make sure Radius Service-Type is set to ‘Authorize’ only, that way it skips the AuthC portion of the rule (we’re only using ISE for Authorization).
That should be everything needed on the ISE side. Let’s see if we can bring it all together now!
Finalizing Setup and Testing
FMC
At this point we should have all the components configured, now it’s just a simple matter of making sure we’ve got everything updated in the FMC VPN Connection Profile.
First, make sure your AAA settings are correctly configured. Authentication should have Azure method selected with your SSO Server. Authorization should reference ISE.
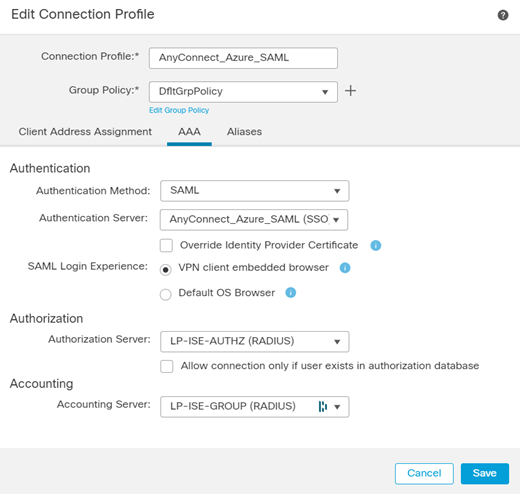
Don’t forget about the Group Policies!
These will provide the unique experience to each user/group type. Be sure to define the appropriate group policies in FMC (including their specific levels of access via ACL). A reminder, ISE will return an attribute that should match the name of the group policy configured in FMC, like (LP-EMPLOYEE).
Azure AD
You should have a ‘Anyconnect’ enterprise application defined, with Basic SAML section updated with meta data from FTD. FTD SSO Server defined with values from Azure and a Conditional Access should also be configured between Azure and Duo (if you followed the Duo guide). You can also include other policy criteria that have to be met, like geolocation, etc.
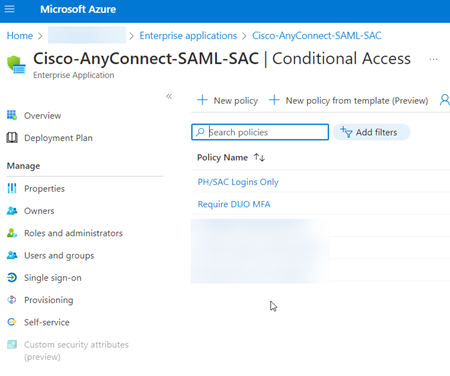
Try and connect, if all goes well, you’ll be online with authorization only to specific areas (as defined by your group policy).
Wrap Up
I know that was a lot, but I hope you found this guide helpful, there were so many components I couldn’t get as granular as I was hoping. If you find yourself stuck, please post your question(s) and I’ll try to respond. If you rather not deal with this at all, we can help roll out from soup to nuts! Please contact sales@lookingpoint.com and we’ll have you up in no time! 😊

Useful References:
Integrating FTD w/ Azure AD YouTube Video from Cisco - https://youtu.be/wgttyx7UFMI
Duo CA Setup - https://duo.com/docs/azure-ca
Michael Lorincz, Network Engineer



