What is Zero Trust? Zero Trust is a framework and attitude towards IT security that centers on the idea that we in the IT field cannot trust anyone or any device on our network. Many systems administrators are well versed in this model. Every employee is assigned a domain joined laptop that is locked down via Group Policy. Those employees are tracked via a user identity using their AD profile that, through security groups, either allow or restrict access to various IT assets (servers, printers, wireless, and/or client VPN). Accounting is enabled to track what the users are accessing and used in the event of a malicious attack to see where the attack originated and who preformed the attack.
OK, so I understand Zero Trust, but where does networking come into play? For the longest time networks were seen as these black pipes; pipes you couldn’t look into but we could see data come in one end and out the other. You could see the raw data to get IP and MAC information but that didn’t help you to understand who that data was for. Because of this limitation we started segmenting the network, we created parallel pipes by creating use specific VLAN’s and using firewalls and Access Control Lists at each end we could start to limit what users could access by placing them in a specific pipe. This worked well in the age of desktop computers and statically placed machines, we could assign those always wired machines to a VLAN and we would know it has the right security policy. But now that we live in a world of mobility where a user could pop up anywhere in our network those traditional security measures no longer work. Zero Trust networks address this issue.
Enter the Zero Trust Framework
When beginning on a journey it is best to know where you are going. This quote from an eBook published by Duo describes the end goal pretty well.
Zero trust is a security model that shifts the access conversation from traditional perimeter-based security and instead focuses on secure access to applications based on user identity, the trustworthiness of their device and the security policies you set, as opposed to the network from where access originates.
https://duo.com/resources/ebooks/achieving-zero-trust-security-in-a-federal-agency
To achieve this end goal there are 5 key areas to focus on:
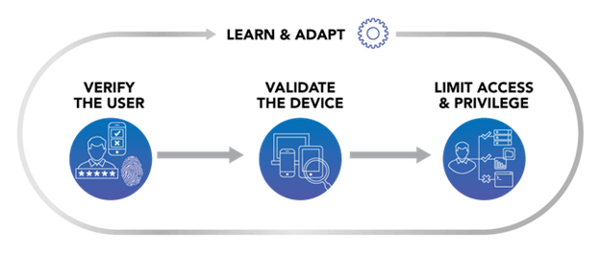
- The first is user identity. This means that anytime a user logs into the network that their credentials are pushed to the network. In this area things like Network Access Control and Multi-Factor Authentication are taken into consideration. Verifying who is logging onto the network and recording this user is key to the rest of the areas.
- Second is device identity. In the same way that we want to verify the users accessing the network, in an age of mobility we want to make sure we know what machines are connecting to the network. In this area things such as device posturing, and BYOD registration are taken into consideration. Again, this is a key element used in the rest of the areas.
- The third area is network access policy. In this area we combine the information gathered in the first two areas and do something with it. In this area 802.1x authentication on access switches and wireless access points can dynamically assign a user to a VLAN, and/or download an access control list and apply it to your port. This means that no matter where you are in the network the security policy assigned to your user using a particular machine will follow you. Additionally, the security policy can change depending on where you access the network. This means that the same user and machine logging in on the wired, wireless, or via client VPN can have access to different applications.
- The fourth area is network monitoring. By network monitoring I don’t mean traditional network monitoring that looks at the uptime or utilization of a device, but as in traffic analysis. In this area things such as netflow collection and context-aware security monitoring are used to monitor for threats. Now that we know the users and devices, and know what access policies they should follow we can now build a complete automated security solution. Knowing how traffic should flow though the network means we also know when malicious traffic is on the network as it tends to go against the traditional flows.
- The last area is to extend security visibility into the data center. With more companies adopting the hybrid cloud model maintaining consistent security policies between the on-prem data center and various cloud services can be a challenge. Workload protection platforms provide insight to possible holes between applications and take measures to reduce east/west security vulnerabilities by creating micro-segmentation. This way if a server has been compromised, security measures are in place to limit the scope of attack. While this area has some overlap with the fourth area, business requirements between the campus and the datacenter are different enough for it to warrant its own area.
Once the fifth area has been completed you and your company have ascended to what some have called Zero Trust Nirvana.
 Zero Trust is an Attitude
Zero Trust is an Attitude
While it seems easy to buy a bunch of products and install them on your network you won’t be able to sustain Zero Trust Nirvana without a change in attitude. The adage “You’re only as strong as your weakest link” holds true with Zero Trust. A security first attitude from both your IT staff and general users should still be maintained; the least privilege concept should still be adopted and users should still be trained against social engineering procedures. Remember that the first area in zero trust is user identity, each user holds a key to the network and can unknowingly give that key to an attacker.
Zero Trust is also designed to supplement traditional security products, not replace them. Anti-malware, and more traditional content blockers and firewalls should still be used because at any time a user could click on that malicious link, providing that backdoor into the network. With Zero Trust think more security layers, not different security layers.
With an ever changing IT landscape and a move to user mobility, the game of securing the network has always been a game of catch up. With the Zero Trust framework we now have a multi-layered, transparent, automated, security mindset that will finally allow us to quickly adapt to our evolving industry in a secure manner.
As always if you have any questions on the Zero Trust Framework above, please reach out to us at sales@lookingpoint.com and we’ll be happy to help!




