
Thinking about migrating from an ASA firewall to a Firepower Threat Defense (FTD) all-in-one appliance? Instead of manually inputting the entire configuration from an ASA to an FTD, Cisco provides a migration tool to help with the transition. This tool, aptly named the firepower migration tool, has limitations but it can help migrate objects, access control lists (ACLs) and network address translations (NATs) that otherwise would have to be manually migrated from the ASA to the FTD. This tool becomes more valuable when there are multiple ASAs with hundreds of ACL entries, objects and NATs.
Platform requirements
The migration tool requires the following to run:
- Windows 10 or MacOS 10.13 or higher
- Google Chrome
Limitations
Here are the limitations of the migration tool:
The following configuration are not migrated because it is not supported by the FTD:
-
- Route based VPNs are not support by FTD.
- Local user accounts.
- Nested object-groups.
The following configuration are not migrated and requires manual configuration after the migration:
-
- VPNs: Anyconnect client vpn or site-to-site vpn
- Dynamic routing
- IP SLAs and tracking
- Device specific configurations such as snmp, syslog, netflow, radius, tacacs, ldap, etc
ASA version needs to be 8.4 and higher.
Migration Process
- Download the migration tool for the desired platform from cisco.com using a CCO account.
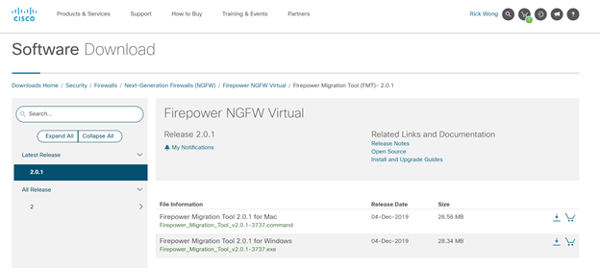
- Run the executable
Note: Do not close the cmd window. Closing this window will exit the migration tool.
- Login with a CCO account to share statistics with Cisco or use the local default account to login
Default local account:
Username: admin
Password: Admin123
-
Select a source for the migration.
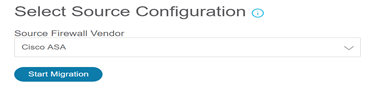
-
Select manual upload of the configuration or connect to ASA as the source of the configuration.
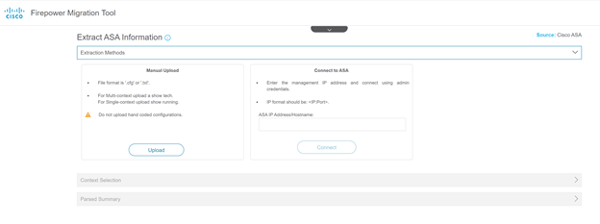
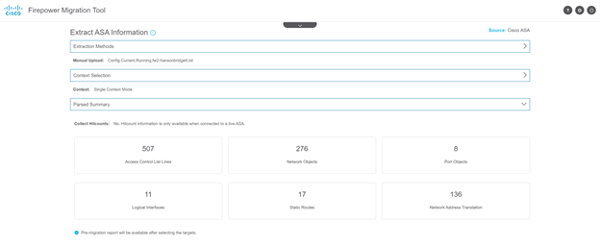
The migration will parse the data from the ASA configuration.
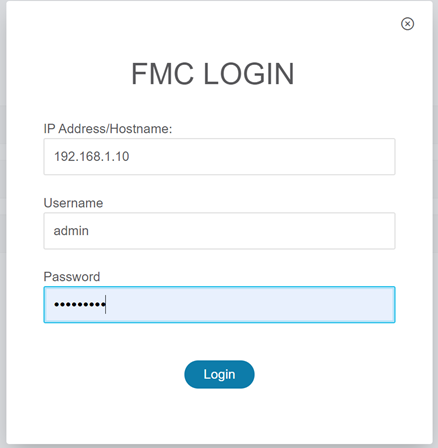
- Connect to the FMC where the FTDs are registered. You can still use the tool if there are no FTDs registered. Interfaces and routes will not be migrated if no FTD is present.
- Select a target FTD to apply the migrated configuration. If no FTD devices are registered with the FMC, interfaces and routes will not be migrated.
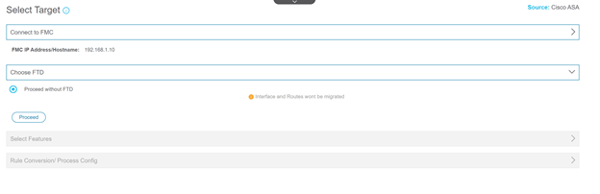
- Select the features to be migrated and start the conversion.
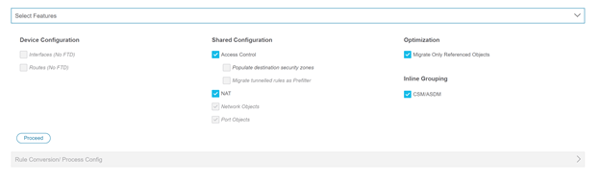

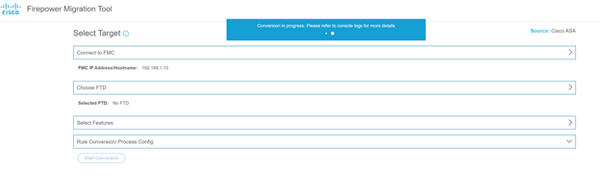
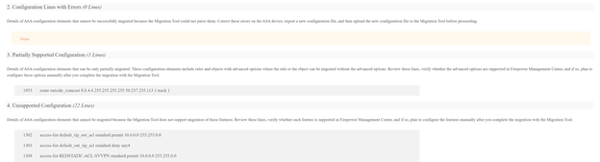
- Download and review the pre-migration report.
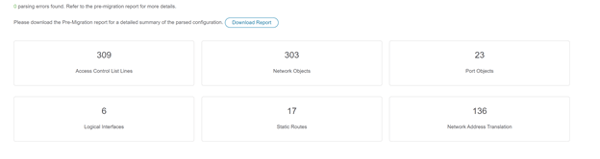
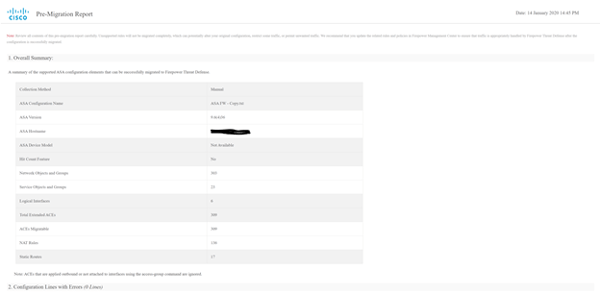
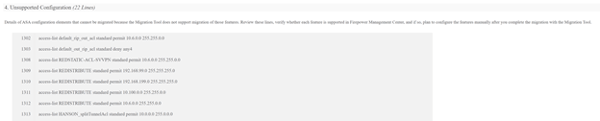
- Map the ASA interfaces and to FTD interfaces and security zones. This section only applies if an FTD is the target device from step 7.
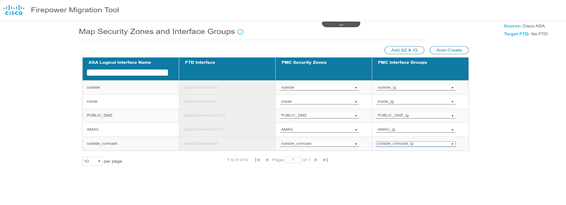
If no FTD target device is selected the Map FTD Interface option is not available.

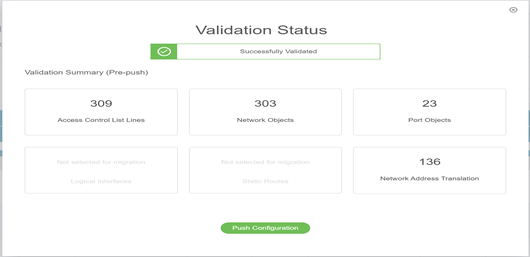
- Review and validate the migrated configuration. Any errors reported during validation will need to be corrected before proceeding.
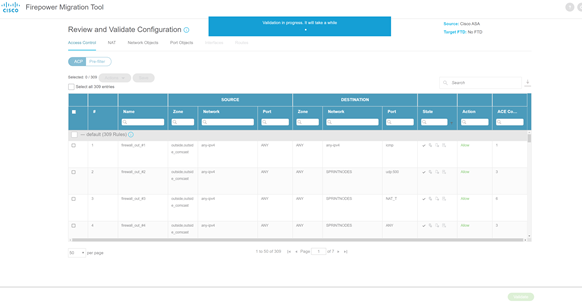
- Push the configuration to the FMC after successful validation.
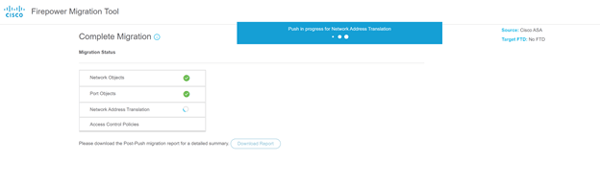
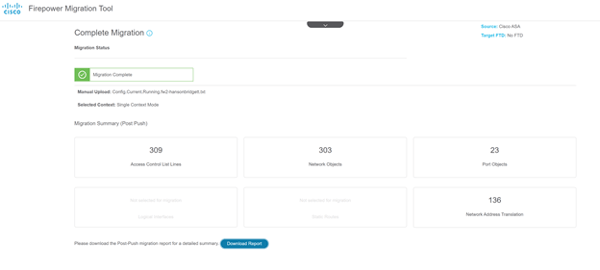
- Download and review the migration report after the migration is complete.
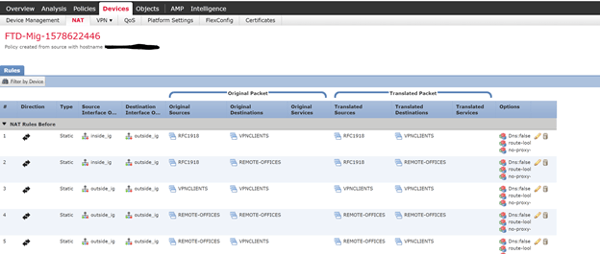
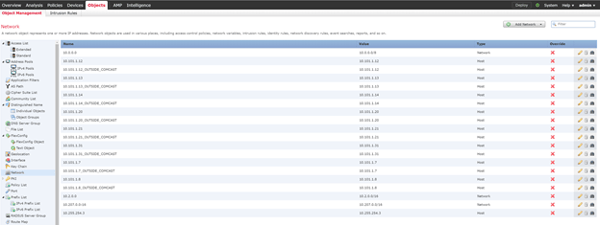
- Login to the FMC. NATs, ACLs and Objects are now populated by the migration tool.
As always if you have any questions on getting Cisco's Firepower set up for you and your business and would like to schedule a free consultation with us, please reach out to us at sales@lookingpoint.com and we’ll be happy to help!

Written By:
Rick Wong, Principal Network Architect




























