In the last entry of this series, we looked at the high-level mechanics involved in using AnyConnect with the ISE Posture module to perform endpoint host inspection (posture) when connecting to an AnyConnect VPN head-end (ASA/FTD). If you haven’t read that one yet, you can find it here!
In this entry, we will be narrowly focused on provisioning the ISE posture module. Enjoy!
Setting the Stage!
We must start somewhere, so let’s make sure we understand where that is! In the scenario covered here, we are going to assume that AnyConnect core VPN client is already installed. But wait, there is more! We are also going to assume that the AnyConnect client was installed via head-end deployment by a Cisco Firepower Threat Defense VPN head-end. But wait, there is more! We are also going to take for granted that the FTD is already configured to process user authentications and/or authorizations using RADIUS to Cisco ISE! That makes our next necessary step to get the ISE Posture module added into the existing AnyConnect client. I know you are as pumped as I am! Let’s get it!
P.S. Pre-deploy options exist as well, but I’ll leave you to DYOR (do your own research) on that approach. Additionally, other “head end” deployment options (Umbrella for example) exist that are not covered here.
A Brief Q/A Monologue
There are multiple hands in the cookie jar when it comes to the client provisioning responsibilities. Not only that, but there are also options too! Options can be great, but when it comes to provisioning ISE Posture, it is the humble opinion of this keyboard that the following questions are answered correctly.
|
Question 1 |
Who deploys/upgrades the AnyConnect VPN Client and the ISE Posture Module? |
|
Answer 1 |
The VPN head-end (so the FTD/ASA)! |
|
Question 2 |
Do the versions of AnyConnect need to match on the ISE Client Provisioning Policy and the VPN head-end? |
|
Answer 2 |
You bet they do! |
|
Question 3 |
Do the AnyConnect versions automatically stay in sync between ISE and ASA/FTD? |
|
Answer 3 |
No, no they do not. Dear Cisco, please make this happen in future land. |
|
Question 4 |
Okay…so what does ISE provision then? |
|
Answer 4 |
The ISE Posture profile and the ISE Posture compliance module (this is different from the ISE Posture module itself.... I know, totally NOT confusing!) |
FMC Provisioning of Posture Module Deployment
The following procedure can be followed to add the ISE Posture module deployment to an AnyConnect Group Policy on a Cisco FMC managed FTD.
Navigate to FMC > Devices > Remote Access
Click on the Name of the Remote Access configuration you wish to modify
Click on Advanced > Group Policies and edit the group policy you wish to add the ISE Posture module deployment to.
Click that little + icon on the AnyConnect > Client Modules menu.
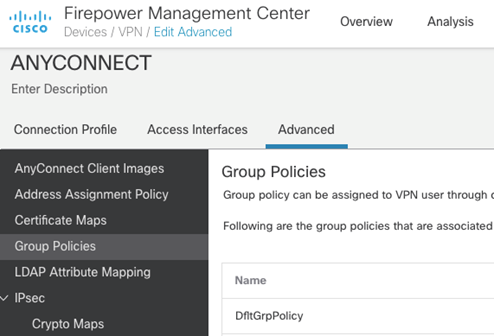
Click that little + icon on the AnyConnect > Client Modules menu.
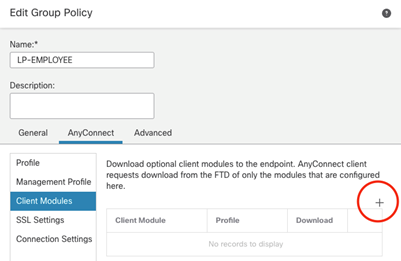
Select the ISE Posture Client Module and check the box to Enable module download. Save, save, and deploy!
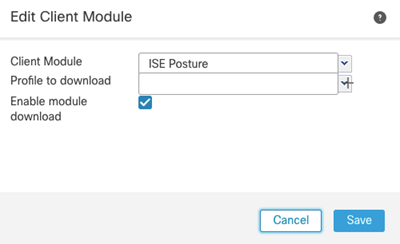
Before the next connection attempt, you can see there is only the VPN module installed on our test AnyConnect client.
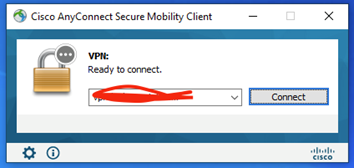
During the next connection attempt, the client is instructed to download the ISE Posture module.
Cisco Identity Services Engine: Provisioning AnyConnect for ISE Posture
Alright! Now we have the ISE Posture Module deployed to our AnyConnect client (System Scan tile). Notice how we have “No policy server detected.” Great segue to the next section!
How Does the Posture Module Discover ISE?
Our ISE Posture module is now deployed to our test AnyConnect client. The next step is to put the necessary configuration in play to allow a new ISE Posture module to locate its master (ISE). There are a couple ways to go about this depending upon what your goals are for user experience. Both methods involve instructing the ASA/FTD (in this case) to redirect certain HTTP traffic to the ISE Client Provisioning Portal. If you are familiar with Monitor Mode, Low Impact Mode, and Closed Mode when it comes to deploying 802.1x authentication on the wired access network, you have similar options/strategies available to you when deploying posture checking with ISE.
In the initial phase of any posture deployment, my preference is to simply monitor the posture status of the endpoints connecting to the network. Therefore, I don’t want users to see any intervention to their network access after completing authentication to the VPN. Saying this another way, we don’t want the user to see this HTTP redirection to the ISE Client Provisioning Portal. We only want the AnyConnect ISE Posture module to see this. To accomplish this goal, the kind folks at Cisco provided the capability to define “Discovery Hosts” to the ISE Posture module. The ISE Posture module sends an HTTP GET request to the discovery host[s], expecting that they will get redirected to the ISE Client Provisioning Portal. The beautiful thing about this discovery host-based discovery process is that the user doesn’t have to see the HTTP redirection occur in their browser. Just what we are after! While we can provision custom discovery hosts, Cisco provides for a default discovery host; enroll.cisco.com. Cisco maintains a public DNS record for enroll.cisco.com which always resolves to the same IP address. Cisco has done their part by programming the ISE Posture module to send an HTTP GET to enroll.cisco.com. Now for our part.
Create a Redirect ACL on the FTD
Back to the FMC, we will provision an ACL object that simply permits HTTP traffic destined to the IP address that enroll.cisco.com resolves to. A quick nslookup tells us that enroll.cisco.com resolves to 72.163.1.80.
Here is our ACL object 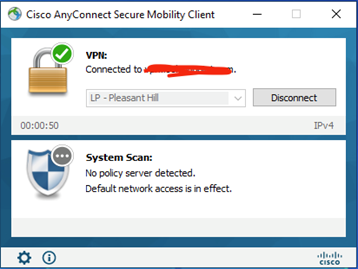
Here we associate this ACL object to
our CoA enabled RADIUS/ISE servers 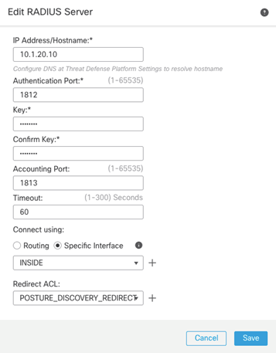
Note: If you are split-tunneling, be sure to split-include the enroll.cisco.com IP address! IMPORTANT!
Now The ISE Configuration
The moment you’ve all been waiting for, the ISE configuration! Our goal here for this blog post is to get the ISE Posture module provisioned. So, surprisingly we will navigate to Work Centers > Posture > Client Provisioning to begin our ISE work.
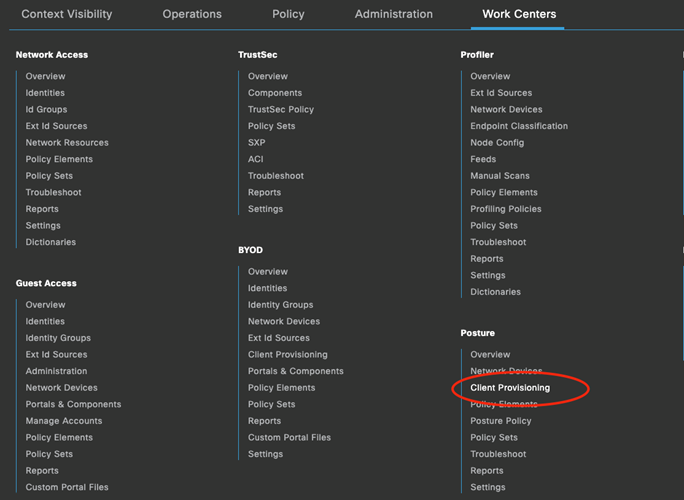
First, we need to add the AnyConnect web deploy package to ISE. This should match the web deploy package installed on the ASA/FTD!
Once is has finished uploading, click Submit!
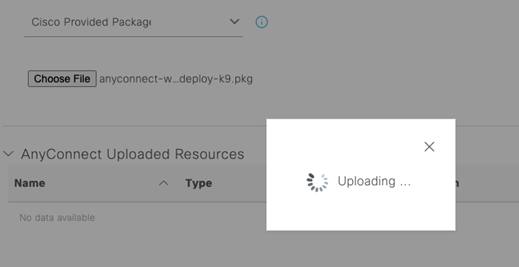
Confirm the hashes match (or just click Confirm ;))!
Next, we are going to add the latest compliance module from Cisco’s site
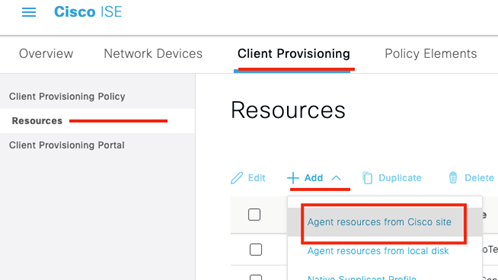
Select the latest compliance module for your operating system and click Save!
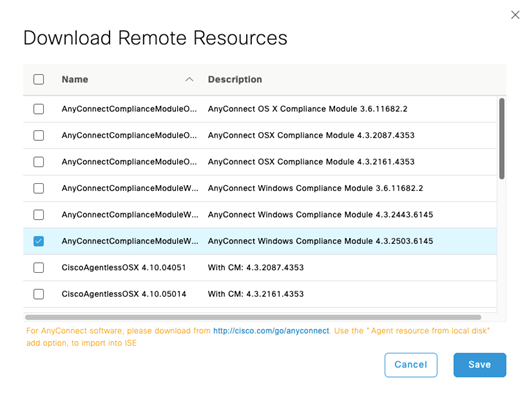
Now we create the Posture Profile!
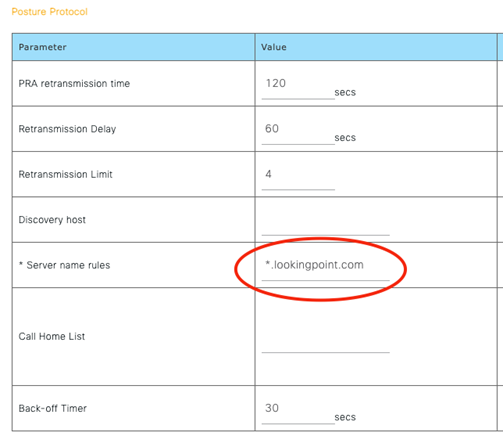
The only thing we MUST fill out on the posture profile are the Server name rules. This defines the ISE server names that the Posture module is allowed to communicate with. This is a security measure to prevent your posture modules installed on corporate owned assets from communicating with an ISE server from another organization, potentially leaking information from your hosts to third parties. For a contractor profile, you could input just a “*”. Save! Almost there!
Now we add the AnyConnect Configuration, which ties all the previous configuration together!
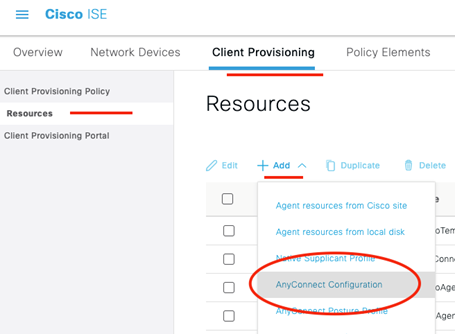
Select the AnyConnect package we uploaded previously. Select the Compliance Module we uploaded previously and leave ISE Posture as the only module selected (it cannot be deselected). Lastly select that ISE Posture profile we created in the previous step. Save! We are so close, hang in there!
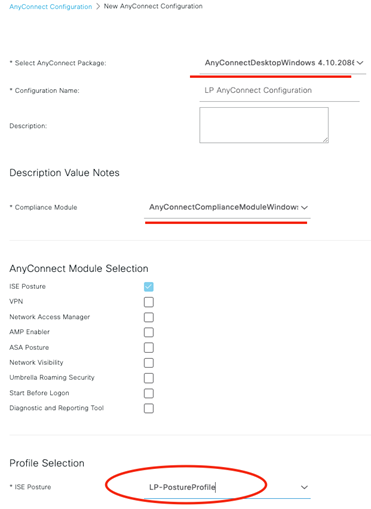
For our last act in ISE provisioning for the posture module, we will assign that AnyConnect Configuration to our Client Provisioning Policy. This policy is used to determine how to provision a client who is redirected to the ISE Client Provisioning Portal.
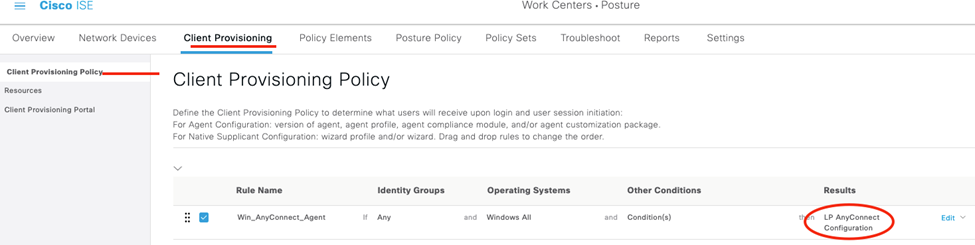
For our last act in ISE, we are going to configure our authorization policy to redirect AnyConnect VPN clients who successfully authenticated to the ISE Client Provisioning Portal.
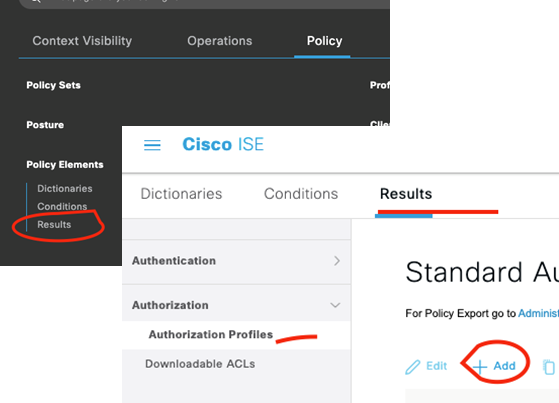
We want to enable Web Redirection on the Authorization Profile and reference the name of the ACL we created previously on the ASA/FTD. Save!
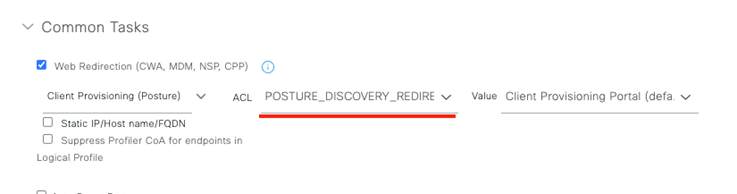
Make sure you update the appropriate Policy Set authorization rule with this Authorization Profile! Now we test!
As always if you have any questions on getting Cisco's ISE set up for you and your business and would like to schedule a free consultation with us, please reach out to us at sales@lookingpoint.com and we’ll be happy to help!
Want the answers to the most asked questions about ISE? Check out our video below!
Dominic Zeni, LookingPoint Consulting Services SME - CCIE #26686




