In the first entry of this series, we looked at the high-level mechanics involved in using AnyConnect with the ISE Posture module to perform endpoint host inspection (posture) when connecting to an AnyConnect VPN head-end (ASA/FTD). In the second entry of this series, we narrowly focused on getting the ISE posture module provisioned. In the third entry, we took stock of all the available posture checks. If you haven’t check those out yet, please do, links below!
First Entry – High Level Overview
Second Entry – ISE Posture Module Provisioning
Third Entry – Available Posture Checks
In this last entry, we will walk through the configuration of a couple commonly used posture checks and provide an example of how to use posture state as a condition in your ISE authorization policy. Enjoy!
Posture Check Configuration
Here we will walk through the configuration of a few commonly used posture checks. For brevity sake, we’ll focus on creating posture checks for Windows OS.
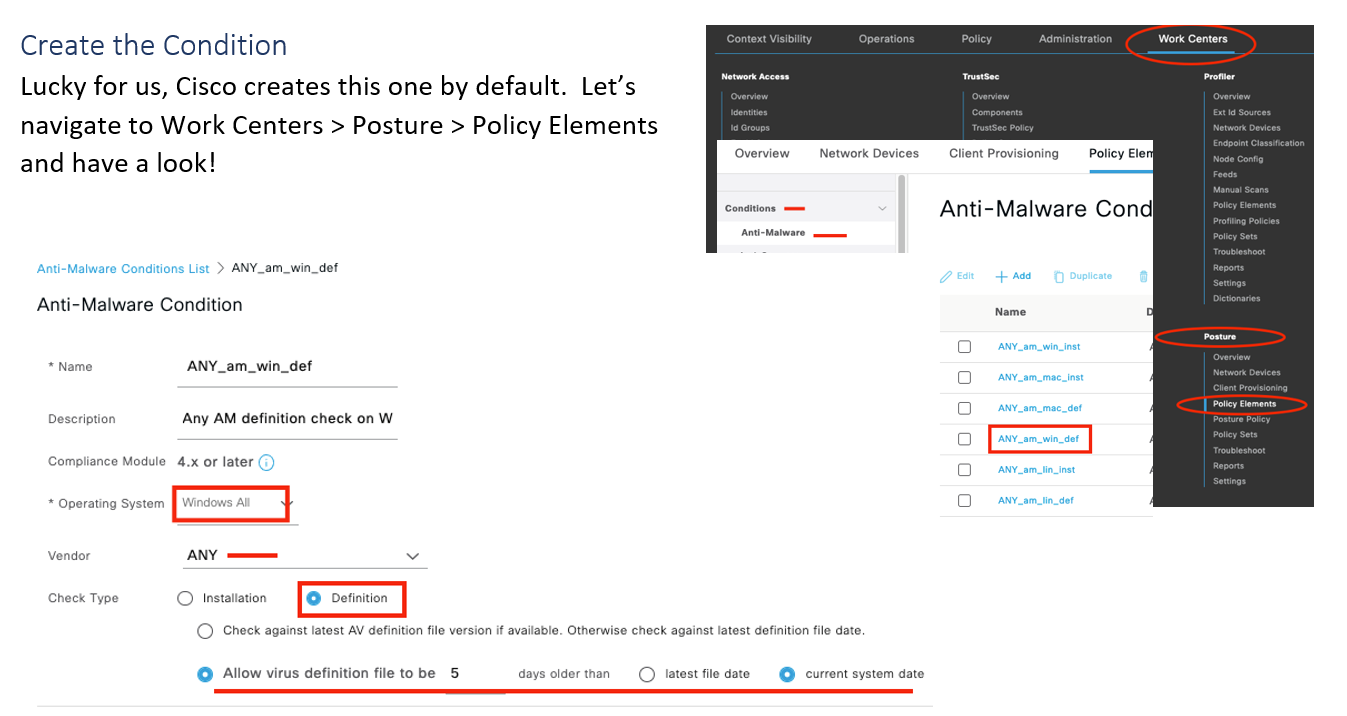
Anti-Malware (AM) Check
This check is applicable to AnyConnect 4.x+. It combines/replaces the functionality of the (now legacy) Anti-Spyware and Anti-Virus checks. Depending on the AM product, you will be able to check for both if the product is installed and if the definitions are up to date within a configurable threshold. In this example, we will setup an AM check for ANY supported AM product to be installed and ensure the definition file has been updated within our admin defined time period. This check works well for non-managed devices where you do not know which AM product the endpoint may have installed. Cisco maintains a list of the supported AM products and their varying levels of support here.
As shown above the default “ANY_am_win_def” condition checks the Windows OS for ANY AM vendor definition file to be 5 days older than the current system date. You can modify this default condition to suit your needs…moving on!
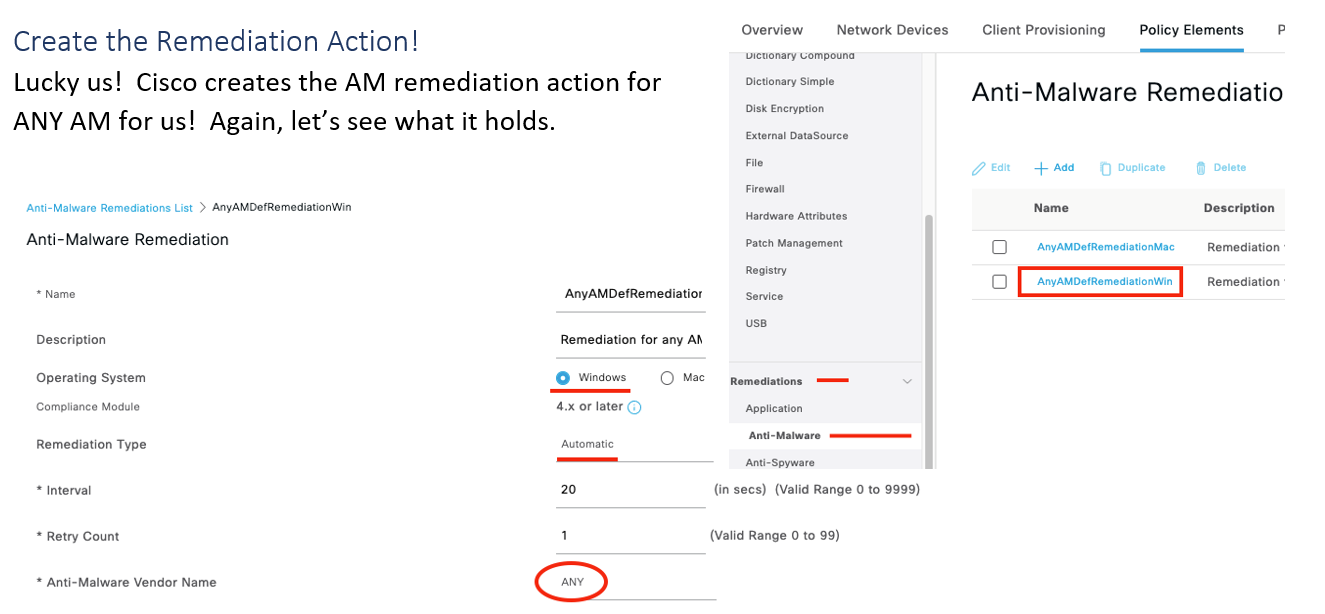
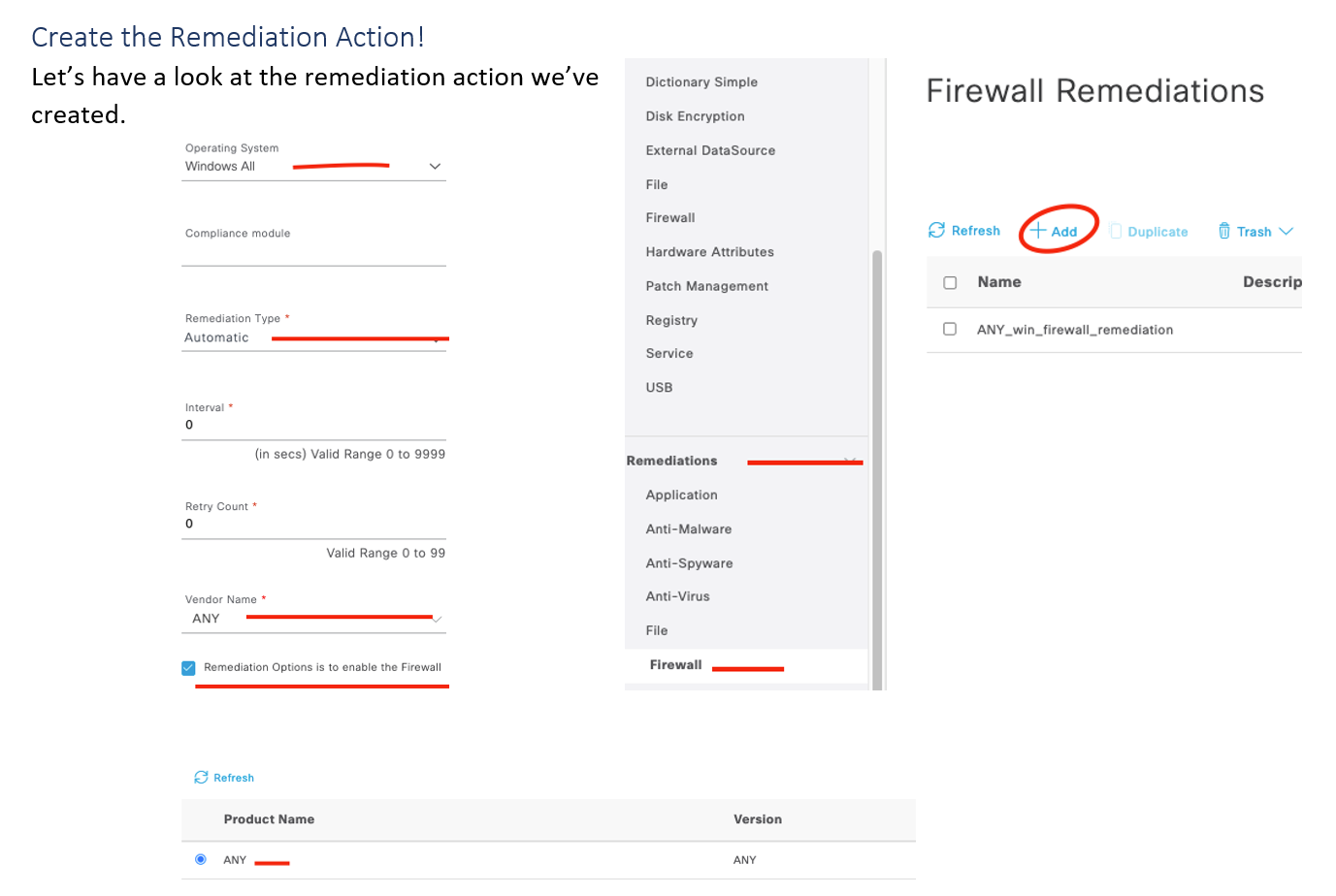
As shown above, this remediation action will be applicable for Windows OS with ANY AM vendor. Also, if automatic remediation is supported on the product (see support matrix), the ISE compliance module will trigger the AM product to update its definitions (posture unknown authorization rule must provide enough network access to reach the update server – typically Internet-only access is sufficient).
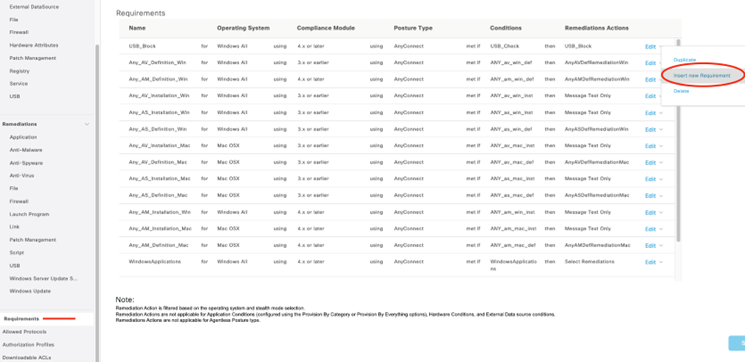
Create the Requirement!
Now that we have the two building blocks for our AM check, we can create the requirement! Once again, Cisco has outdone itself by creating this requirement by default. Let’s check it out.
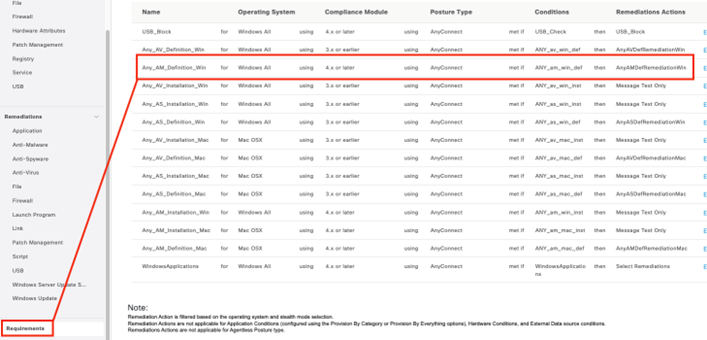
Alright! We have finished creating our requirement for the AM check. Keep in mind, it is not applied to a posture policy yet! We’ll get to that after we create our next couple checks. Speaking of those, let’s get going!
Disk Encryption Check
We will create a disk encryption check to ensure that the all the data on disks of endpoints connecting to our network is encrypted.
Create the Condition
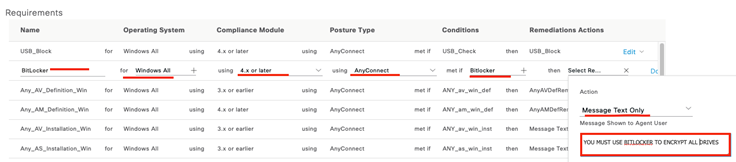
Unlike our AM conditions, which we used the Cisco provided defaults for, we need to create our Disk Encryption condition. Here we created one called “Bitlocker”. Let’s look at what it contains!
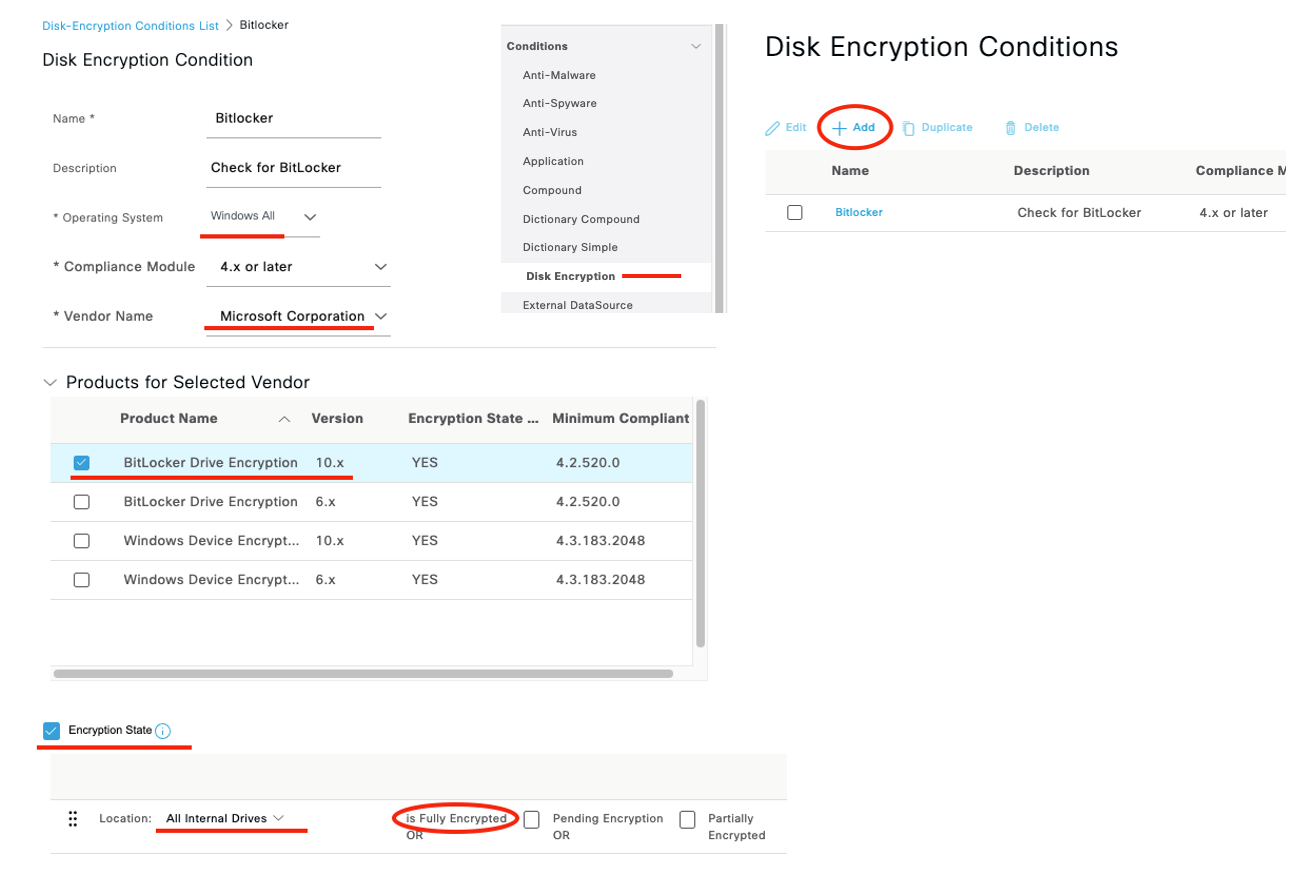
As we can see this condition is checking Windows OS for BitLocker Drive Encryption 10.x and checking the encryption state to ensure all internal drives are fully encrypted. Good. Real Good. Remediation actions are not available for disk encryption (we can display a message, if desired, as a part of our requirement). Let’s build that requirement!
Create the Requirement!
After navigating to the Requirements menu, click the drop-down next to any existing requirement and select to Insert New Requirement.
Our newly created disk encryption requirement is shown below. The remediation action has been set to Message Text Only and a freeform message text was configured.
Firewall Check
With this check, we will simply ensure that an endpoint firewall is active on the endpoint. We will make this check like our AM check in that we are allowing ANY firewall to be active on the endpoint as opposed to a particular vendor’s endpoint firewall.
Create the Condition!
Again, no Cisco default condition created for this, so we’ll add our own as shown here.
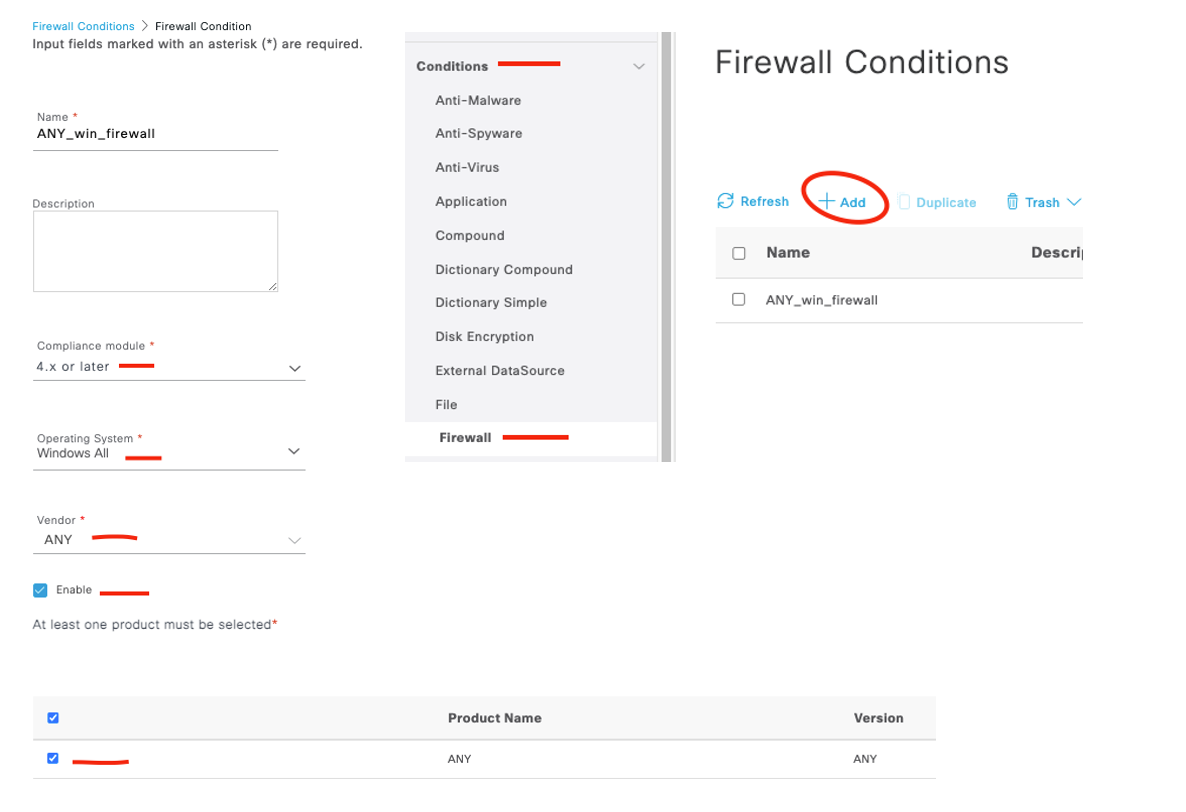
This condition applies to Windows OS and is met if the endpoint has any supported endpoint firewall enabled. Alright, lets create the remediation (noticing a pattern yet?)! Let’s go!
As shown above, this remediation will apply to Windows OS, and it will automatically enable the endpoint firewall. Cool, next up the requirement!
Create the Requirement!
After navigating to the Requirements menu, click the drop-down next to any existing requirement and select to Insert New Requirement. Our new requirement for the Windows firewall is shown below.
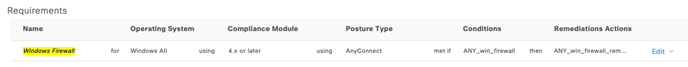
Alright, alright, now that all the posture check requirements have been made, we need to create our posture policy. Onward!
Posture Policy
When an endpoint is in the posture flow, ISE examines the posture policy to determine which requirements a particular endpoint needs to meet. In this example, we will create a posture policy that applies to all Windows endpoints and assigns the three requirements we’ve just created.
Navigate to Work Centers > Posture > Posture Policy
Our new policy is shown below, tying all our requirements together into a single posture policy rule!
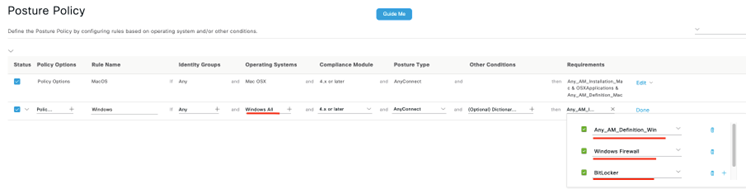
At this point, we’ve created everything needed from the posture perspective. Endpoints connecting to our AnyConnect head end will begin posture evaluation against the three requirements we’ve defined.
BUT (that’s a big but)
We haven’t created any authorization rules that use the posture status of our endpoints to provide differentiated network access. This means that no matter if you meet a requirement or fail a requirement, no enforcement action (in terms of network access) is taken. Let’s take care of that big but in the next section.
Policy Set Authorization Rules Based on Posture Status
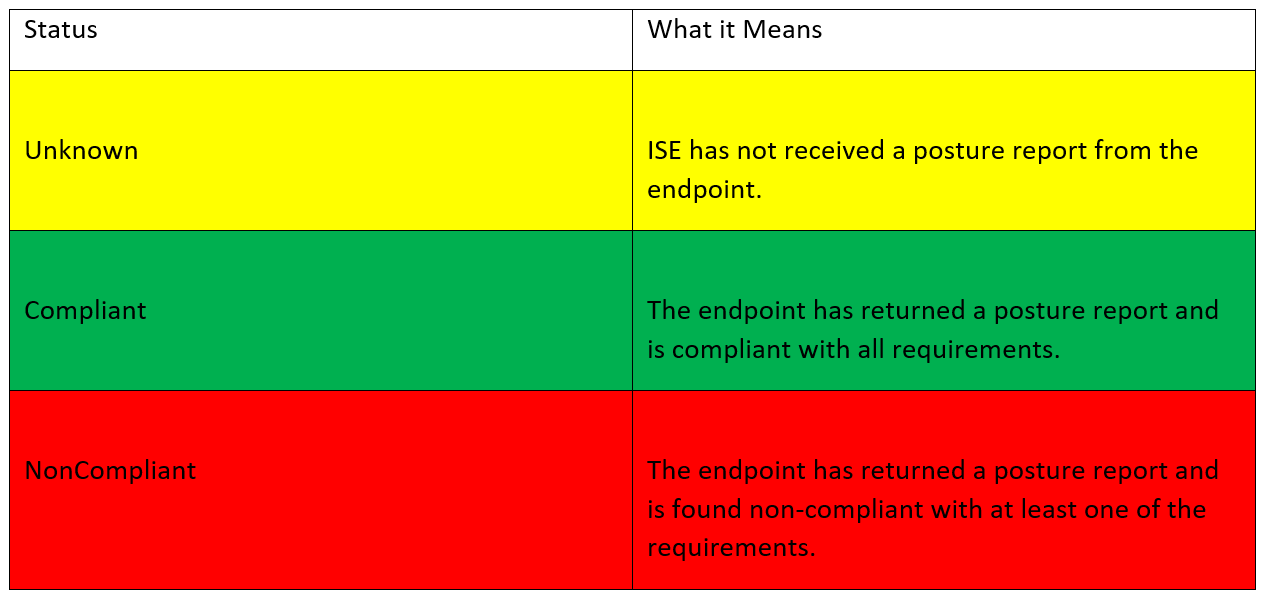
There exist three possible posture statuses that can be used in our authorization policy conditions.
Below is an example of the posture conditions being used in an authorization policy.
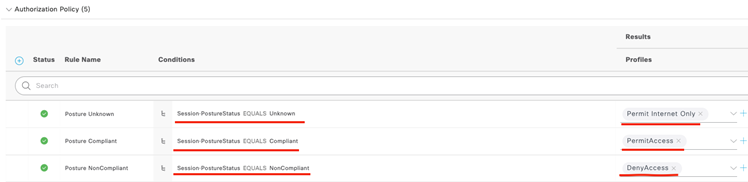
Finally, our network is protected. Whew, what a relief!
What’s Next?
I hope you’ve enjoyed this series of blog posts on ISE Posture with AnyConnect VPN. Stay tuned for more to come! Thanks for reading!
As always if you have any questions on getting Cisco's ISE set up for you and your business and would like to schedule a free consultation with us, please reach out to us at sales@lookingpoint.com and we’ll be happy to help!
Want the answers to the most asked questions about ISE? Check out our video below!
Dominic Zeni, LookingPoint Consulting Services SME - CCIE #26686